Boot Flow
Note: | This chapter is currently under review. We recommend that before you use this information, check with your NVIDIA® customer engineer (CE) for verification of its accuracy. |
This topic describes the boot flow for NVIDIA® Tegra® code-name Parker for native environments.
Responsibilities of the Boot Software
The primary functionality of the different components of boot software is initialization of SOC (System On a Chip), including MC/EMC initialization and CPU initialization; setting up the security parameters; loading different firmware; maintaining Chain of Trust; setting memory carveouts for different firmware; flashing the device; and booting to the OS. Boot software also performs other operations defined by product requirements, including but not limited to display (HDMI/DSI), displaying the boot logo, boot OS specific update mechanisms and OS specific boot methods.
High Level Tegra Software Boot
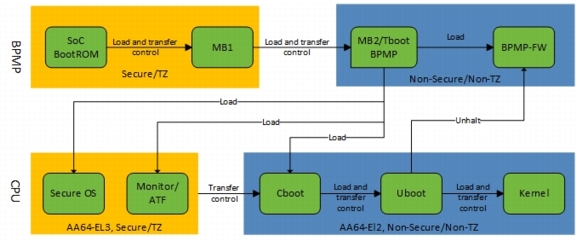
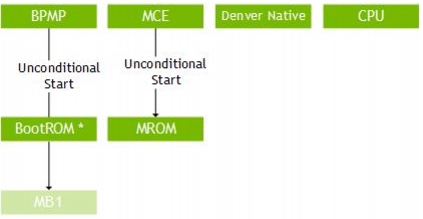
The following diagram illustrates the flow of control in the boot software.
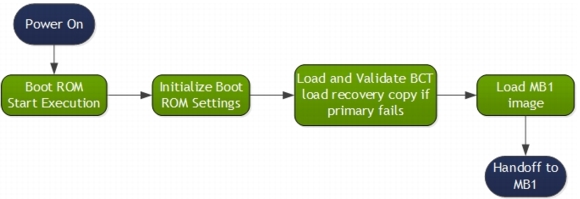
BootROM
The BootROM (BR) is hard-wired in the Tegra chip. It initializes the Boot Media and loads Microboot1 (MB1) from the Boot Media.
Multiple copies of the BR-BCT (Boot Configuration Table) are stored at the start of the Boot-Media. The BR-BCT contains configuration parameters used by the BootROM for hardware initialization.
The BCT also contains information about the boot loader (BL), including:
•Size
•Entry point
•Load address
•Hash
The BootROM uses this information to verify and load the boot loader. The following diagram shows the boot flow.
Boot Loader Components
The boot loader and flash components are:
•Common Driver Framework (CDF)
•Microboot1 (MB1)
•TBoot-BPMP (MB2)
•CPU-BL
•TBoot-CPU
•CBoot
•U-Boot
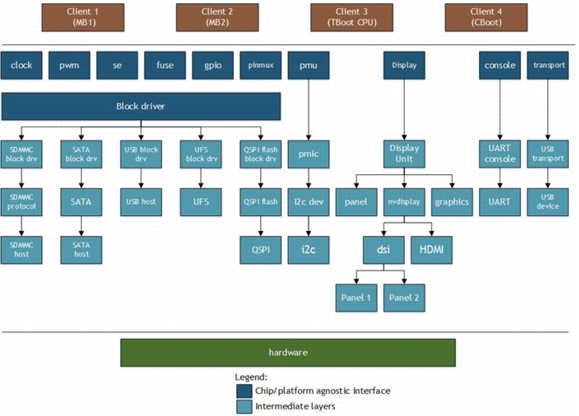
Common Driver Framework
MB1, TegraBoot-BPMP, and TegraBoot-CPU/CBoot each needs to use one of several drivers. Moreover, some libraries are common across the boot loader components. Instead of using separate sets of drivers and libraries, the binaries share a common pool of drivers and libraries called the Common Driver Framework (CDF).
Note: | U-Boot does not support or use CDF as it’s built separately from the NVIDIA-proprietary bootloader software. |
The following diagram shows the software design architecture using CDF:
CDF consists of the following:
•Storage drivers like eMMC, QSPI, SATA
•Host interface drivers like UART, USB
•Display drivers
•Debug and Console library
•Libraries of other modules like clock, SE, PMIC, timer, fuse, GPIO, PWM, EEPROM, keyboard, and PSCI
•Software libraries like the cryptographic, transport, partition manager, sparse, and transport libraries
•A decompression library that supports LZF, Zlib, and LZ4
•clib, a dynamic memory allocation library, and a cache library
The CDF is in the following location:
<top>/vendor/nvidia/tegra/bootloader/partner/common/
and
<top>/vendor/nvidia/tegra/bootloader/partner/t18x/common/
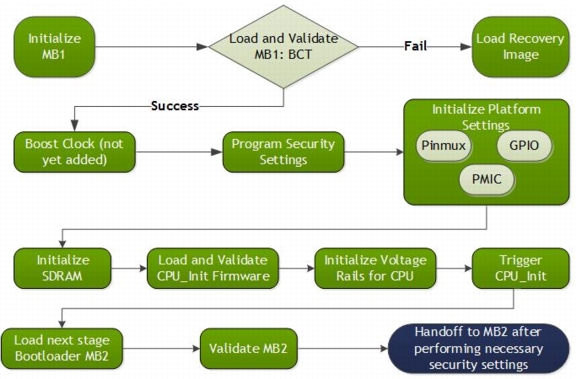
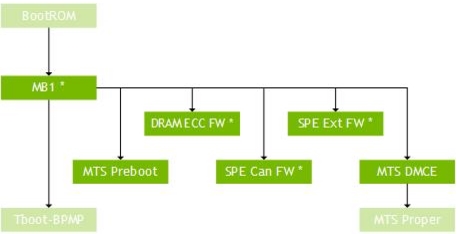
Microboot1
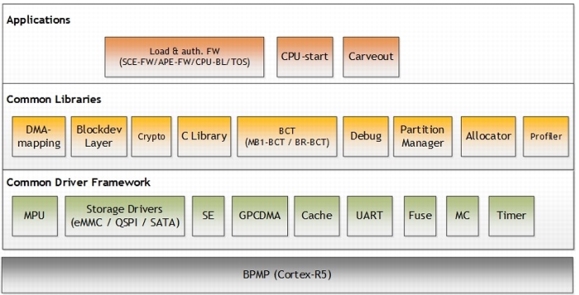
Microboot1 (MB1) is the first boot software component loaded by BR in SysRAM, and runs on BPMP. MB1 is considered as an extension to BR. MB1 provides extensive flexibility to alter or fix the boot sequence. This component also implements some delicate functionality like Denver initialization and security fabric changes.
Because MB1 is an extension to BootROM, it is signed and encrypted by an NVIDIA owned key (separate keys residing in BootROM). The following diagram shows the flow of control in MB1.
MB1 is responsible for:
•Firmware initialization, include MTS preboot, SPE, and CAN
•Platform configuration, which includes configuring pinmux/GPIO configuration, pad settings, prod settings, initializing certain rails including rails required by CPU, memory, GPU etc., PMIC commands required by BR, and SCR configuration
•Initialize the SDRAM based on the MB1 boot configuration table (MB1-BCT)
•Load the firmware that initializes the CPU complex (CCplex)
•Set the security settings
•Configure pinmux/GPIO for the SoC
•Program the PMIC for the VDD_CPU and VDD_DDR rails
•Creating carveouts
•Support flashing (available as a different mb1_recovery.bin binary)
•Support “RCM boot” by downloading a blob that contains the binaries, and loading binaries from that blob.
•Load the next stage boot loader, TBoot-BPMP (MB2)
•Support SC7
MB1 is owned by NVIDIA, and so is provided as a binary in the BSP package. Although it is provided as a binary, you can configure its behavior for a specific platform using its Boot Configuration Table, called MB1-BCT. MB1 reads MB1-BCT to configure the platform.
TegraBoot
TegraBoot is the boot loader component that executes after MB1. This component is divided into two portions: TBoot-BPMP (MB2) and TBoot-CPU, depending on the processor on which they are executing. Both are released to OEMs as source code for reference implementation.
TegraBoot-BPMP(tboot-BPMP)
This portion of TegraBoot runs on BPMP. There are two variants of TegraBoot-BPMP (MB2), one used for cold boot and the other for recovery boot. Both are generated using different configuration files and make files.
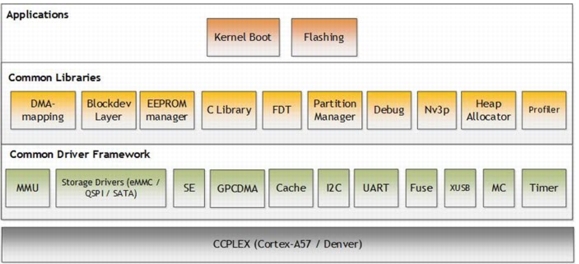
TBoot-BPMP is responsible for:
•Loads and initializes firmware (FW) components such as SCE-FW, APE-FW, BPMP-FW, TOS
•Creates carveouts
•Completes CPU initialization
•Loads the next stage boot loader
•Supports flashing
•Supports “RCM boot”
•Reads PMIC reset reason
•Loads the bootloader device tree and passes the device tree load address to CPU-BL
•Gives control to BPMP-FW
The following block diagram shows the components of TBoot-BPMP:
TegraBoot-CPU
TegraBoot-CPU is a component of TegraBoot that runs on the CPU. Use TegraBoot-CPU to flash the device. You can also use TegraBoot-CPU for “RCM boot,” whose flow is very similar to a cold boot except that the binaries are transferred from the host over USB and are loaded directly to SDRAM. TOS and BPMP-FW are not loaded in this path.
TegraBoot-CPU is responsible for:
•Flashing
•RCM boot
As soon as the CPU starts running, the CPU starts in EL3 mode. TegraBoot-CPU executes a trampoline code which changes the processor mode from EL3 to EL2. It then initializes USB and starts the 3P protocol to flash the device.
For normal flashing TegraBoot-CPU takes the binaries from the host one by one and flashes them to the device. In case of RCM boot, it takes the binaries from the blob downloaded by MB1. The binaries are not flashed on to the device.
TBoot-CPU can also support cold boot by integrating the relevant libraries (linuxboot, etc.). However this version of TBoot-CPU is not tested or maintained.
The following block diagram shows the components of TBoot-CPU:
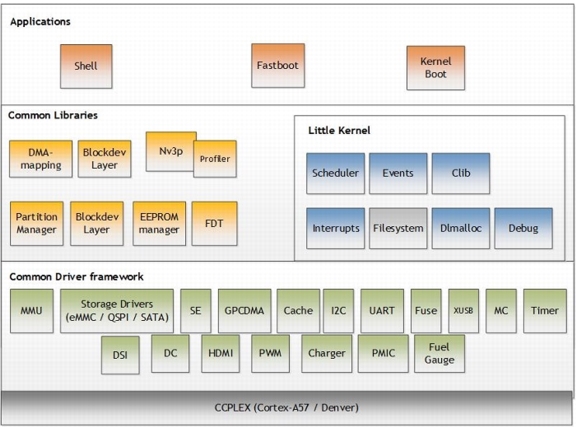
CBoot
CBoot is the primary CPU boot loader used on mobile platforms in the cold boot path. CBoot is feature-rich boot loader used for cold boot. In addition to booting the kernel, it also supports display, boot logo, and verified boot.
CBoot is based on the Little Kernel (LK) open source boot loader. CBoot primarily uses the interrupt and scheduling frameworks of LK. Cboot uses CDF for frameworks, drivers, and libraries.
As soon as the CPU starts running, CBoot starts in EL3 mode and begins executing TOS. TOS completes its initialization and passes control to CBoot in EL2 mode.
BL and Kernel will use separate device trees stored in separate partitions. CBoot is responsible for:
•Parsing the CPU-BL parameters and initializing the boot loader device tree
•Booting to the kernel or chaining to U-Boot to boot the kernel
•Supporting the update mechanism
•Loading the recovery kernel
•Verified boot
The following block diagram shows the components of CBoot:
U-Boot
U-Boot is the default boot loader for NVIDIA® Tegra® Linux Driver Package (L4T). For information on U-Boot, refer to
U-Boot Customization.
TegraFlash
TegraFlash is the host software component primarily responsible for flashing binaries onto the device.
For more information about TegraFlash, see the following:
•Boot Configuration Tables
Security
This section explains the security in the BDK.
Validation of Binaries
All of the binaries involved in the boot process have a generic header (except MB1). The binary is appended to the generic header. The header stores the signature of the binary, which is used for validation in secure boot.
Boot Binaries and Associated Signing
The following table summarizes the boot binaries available in Tegra Code-name Parker and their respective signing authorities.
Boot Binary | Signing Authority |
BRBCT | OEM generated binary, signed by OEM |
MB1BCT | OEM generated binary, signed by OEM |
MB1 | NVIDIA provided binary, signed/encrypted by NVIDIA, OEM will sign/encrypt again |
MTS-Preboot | NVIDIA provided binary, signed/encrypted by NVIDIA, OEM will sign/encrypt again |
MTS-Package (MTS-DMCE + MTS-Proper) | Signed/encrypted separately by NVIDIA, OEM will sign/encrypt again. |
SPE-CAN-FW | OEM owned binary, signed/encrypted by OEM. |
TBoot-BPMP | NVIDIA provided reference code, ultimately OEM owned, signed/encrypted by OEM. |
TBoot-CPU | NVIDIA provided reference code, ultimately OEM owned, signed/encrypted by OEM. |
APE-FW | NVIDIA offers a choice between an NVIDIA signed/encrypted binary and an unencrypted binary for the OEM to sign/encrypt with their board-specific DTB choice. |
SPE-FW | NVIDIA offers a choice between an NVIDIA signed/encrypted binary and an unencrypted binary for the OEM to sign/encrypt with their board-specific DTB choice. |
SCE-FW | NVIDIA offers a choice between an NVIDIA signed/encrypted binary and an unencrypted binary for the OEM to sign/encrypt with their board specific DTB choice. |
CPE-FW | NVIDIA offers a choice between an NVIDIA signed/encrypted binary and an unencrypted binary for the OEM to sign/encrypt with their board-specific DTB choice. |
BPMP-FW | NVIDIA offers a choice between an NVIDIA signed/encrypted binary and an unencrypted binary for the OEM to sign/encrypt with their board-specific DTB. |
CBoot | NVIDIA provided reference code, ultimately OEM owned, signed/encrypted by OEM. |
TOS | NVIDIA provided reference code, ultimately OEM owned, signed/encrypted by OEM. |
SC7-FW | NVIDIA provided binary, signed by NVIDIA, OEM will sign/encrypt again. |
BL-DTB | NVIDIA provided reference code, ultimately OEM owned, signed/encrypted by OEM. |
U-Boot | NVIDIA-adapted OSS code. Unsigned/Unencrypted? |
Secure Boot
Secure boot provides a system of cryptographic checks at each stage of the boot process. These checks ensure the integrity of all of the system software that is executed, preventing any unauthorized or maliciously modified software from being run.
The secure BootROM is responsible for initializing the hardware root of trust (RoT) in the Tegra BSP.
Cryptography is enabled as follows:
•Authentication: RSA2048
•Encryption: AES-CBC128
Supported boot devices include:
•eMMC
•QSPI
Secure Boot Overview
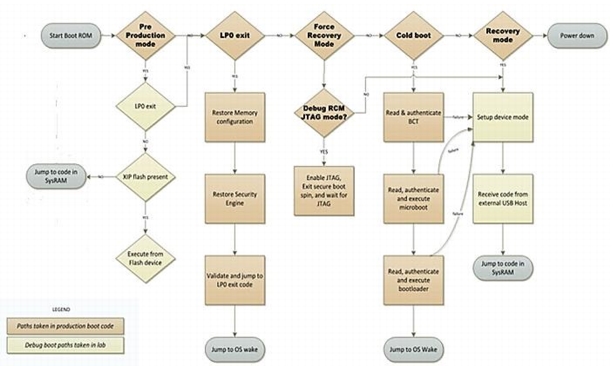
The following diagram shows the flow of secure boot functionality.
If authentication fails, the Boot ROM automatically goes into USB Recovery mode and waits for input via the USB. The Boot ROM never yields control from Recovery Mode except to authenticated code or error messages.
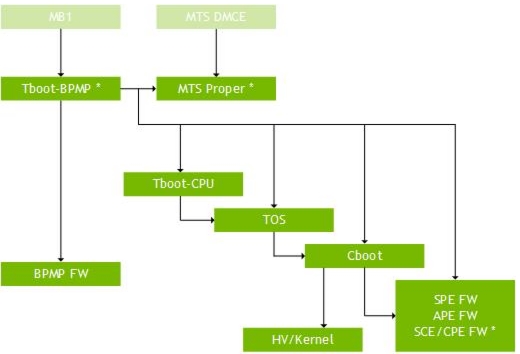
Secure Boot Flow
The following three diagrams show the flow of secure boot stage by stage. Light colored blocks indicate transitions from one diagram to the next.
Each element marked with an asterisk (“*”) has a note below the diagram.
•BootROM: Loads BRBCT and establishes a trusted OEM public key by computing the hash and comparing it to the fuse settings. It then verifies the BCT using the OEM authority (i.e. the public key).
•MB1: Loads MTS Preboot and verifies it using the double verification mechanism. It first verifies the OEM credential, then the NVIDA credential (using MAK/MDK).
Once the MTS Preboot starts to execute by DB0, MTS initializes SDRAM and then loads MTS Package (MTS DMCE and MTS Proper). It verifies and decrypts the entire package, except that it does NVIDIA verification and decryption only on the MTS DMCE portion of the package.
When MTS-related processing is complete, MB1 loads TBoot-BPMP and verifies it using the OEM authority only, and then passes control to it.
•DRAM ECC FW: If required by the platform, MB1 checks whether the boot was started by a reset caused by a two-bit ECC error. If it was, MB1 runs DRAM ECC FW to update the blacklist page and reset the system again. DRAM ECC FW is verified by the OEM authority.
•SPE FWs (SPE Can and SPE Ext): MB1 optionally loads these components after MTS Preboot starts, DRAM is operating, and MTS Package has been loaded and authenticated. In most cases only the smaller SPE Can FW is loaded here; SPE Ext FW is loaded at a later stage.
The SPE FW is typically signed by the OEM authority, but may also be signed by the NVIDIA authority. MB1 identifies the signing requirement from the SignType field of the generic signature header.
SPE Authentication/Decryption keys are used for the NVIDIA authority.
TBoot-BPMP: This is the main binary loader in the boot flow. It loads the binaries that are required to start CPU execution. These binaries are owned by the OEM, and are verified and decrypted using the OEM authority.
After the CPU has started executing the main boot path, TBoot-BPMP loads the coprocessor FWs. Each of these FWs may be verified and decrypted by the OEM authority or the NVIDIA authority, but not by both.
After all components have been loaded, the boot path BPMP code exits and the CPU software resets it into execution of the BPMP FW.
In the distributed BSP, TBoot-BPMP loads the following binaries:
•TBoot-CPU/CBoot
•TOS
•Coprocessor firmware:
•SPE FW
•APE FW
•SCE/CPE FW
•BPMP FW
The OEM controls loading of these binaries, and may include or exclude components as appropriate.
SPE, APE, and SCE/CPE FWs: This firmware is loaded by TBoot-BPMP, but is later started by CBoot. Each firmware may be verified and decrypted by the OEM authority or the NVIDIA authority, but not by both.
Build System
TBD - Need build instructions in tmp mentioned by Tom Warren for this section.