802.1X Interfaces
The IEEE 802.1X protocol provides a way to authenticate a client (called a supplicant) over wired media. It also provides access for individual MAC addresses on a switch (called the authenticator) after an authentication server authenticates the MAC addresses. The authentication server is typically a RADIUS server.
A Cumulus Linux switch acts as an intermediary between the clients connected to the wired ports and the authentication server, which is reachable over the existing network. EAPOL operates on top of the data link layer; the switch uses EAPOL to communicate with supplicants connected to the switch ports.
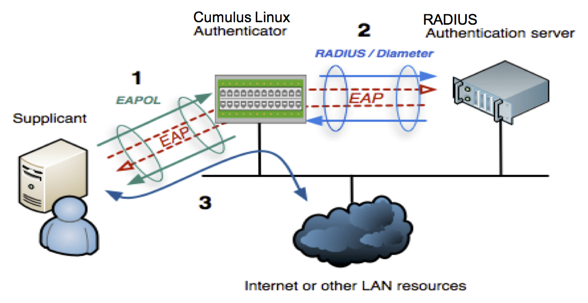
Cumulus Linux implements 802.1x using a modified version of the Debian hostapd package to support auth-fail and dynamic VLANS with MBA and EAP authentication for 802.1x interfaces.
- Cumulus Linux supports 802.1X on physical interfaces (such as swp1 or swp2s0) that are bridge access ports; the interfaces cannot be part of a bond.
- Routed interfaces, bond interfaces, and bridged trunk ports do not support 802.1X.
- To enable 802.1X on an access-port, it must be a member of the default NVUE bridge
br_default. - eth0 does not support 802.1X.
- Cumulus Linux tests 802.1X with only a few
wpa_supplicant(Debian), Windows 10 and Windows 7 supplicants. - Cumulus Linux supports RADIUS authentication with FreeRADIUS and Cisco ACS.
- 802.1X supports simple login and password, and EAP-TLS (Debian).
- 802.1X supports RFC 5281 for EAP-TTLS, which provides more secure transport layer security.
Mako template-based configurations do not support 802.1X.
Configure the RADIUS Server
Before you can authenticate with 802.1x on your switch, you must configure a RADIUS server somewhere in your network. Popular examples of commercial software with RADIUS capability include Cisco ISE and Aruba ClearPass.
You can also use open source versions of software supporting RADIUS such as PacketFence and FreeRADIUS. This section discusses how to add FreeRADIUS to a Debian server on your network.
- Do not use a Cumulus Linux switch as the RADIUS server.
- You can configure up to three RADIUS servers (in case of failover).
To add FreeRADIUS on a Debian server:
root@radius:~# apt-get update
root@radius:~# apt-get install freeradius
After you install and configure FreeRADIUS, the FreeRADIUS server can serve Cumulus Linux running hostapd as a RADIUS client. For more information, see the FreeRADIUS documentation.
Configure 802.1X Interfaces
- All the 802.1X interfaces share the same RADIUS server settings. Make sure you configure the RADIUS server before you configure the 802.1X interfaces. See Configure the RADIUS Server above.
- You must configure 802.1X on a bridged interface. To configure a bridge, refer to Ethernet Bridging - VLANs.
- NVUE enables BPDU guard when you enable 802.1X on an interface; the interface goes into a protodown state if it receives BPDU packets.
To configure an 802.1X interface:
- Required: Provide the 802.1X RADIUS server IPv4 or IPv6 address. If you want to specify more than one server, provide the priority for each server (a value between 1 and 3). If you specify just one server, Cumulus Linux sets the priority to 1. You can also specify a VRF for outgoing RADIUS accounting and authorization packets. A VRF is optional.
- Required: Provide the 802.1X RADIUS shared secret.
- Required: Enable 802.1X on an interface.
- Optional: Change the default 802.1X RADIUS accounting port. You can specify a value between 1000 and 65535. The default value is 1813.
- Optional: Change the default 802.1X RADIUS authentication port. You can specify a value between 1000 and 65535. The default value is 1812.
- Optional: Provide the reauthentication interval for EAP. You can set a value between 0 and 86640. The default value is 0 (disabled). This setting only applies to EAP-based authentication; it does not apply to MBA.
- Optional: Set a fixed IP address for the RADIUS client to receive requests.
Changing the 802.1X interface settings does not reset existing authorized user ports. However, removing all 802.1X interfaces or changing the RADIUS server IP address, shared secret, authentication port, accounting port, or EAP reauthentication interval restarts hostapd, which forces existing, authorized users to reauthenticate.
The following example:
- Sets the 802.1X RADIUS server IP address to 10.10.10.1 and the shared secret to
mysecret. - Enables 802.1X on swp1 through swp3.
cumulus@switch:~$ nv set system dot1x radius server 10.10.10.1 shared-secret mysecret
cumulus@switch:~$ nv set interface swp1,swp2,swp3 dot1x eap enabled
cumulus@switch:~$ nv config apply
The following example:
- Sets the 802.1X RADIUS server IP address to 10.10.10.1 and the VRF to BLUE.
- Sets the 802.1X RADIUS shared secret to mysecret.
- Sets the 802.1X RADIUS authentication port to 2813.
- Sets the 802.1X RADIUS accounting port to 2812.
- Sets the fixed IP address for the RADIUS client to receive requests to 10.10.10.6.
- Sets the EAP reauthentication interval to 40.
- Enables 802.1X on swp1, swp2, and swp3.
cumulus@switch:~$ nv set system dot1x radius server 10.10.10.1 vrf BLUE
cumulus@switch:~$ nv set system dot1x radius server 10.10.10.1 shared-secret mysecret
cumulus@switch:~$ nv set system dot1x radius server 10.10.10.1 authentication-port 2813
cumulus@switch:~$ nv set system dot1x radius server 10.10.10.1 accounting-port 2812
cumulus@switch:~$ nv set system dot1x radius client-src-ip 10.10.10.6
cumulus@switch:~$ nv set system dot1x reauthentication-interval 40
cumulus@switch:~$ nv set interface swp1,swp2,swp3 dot1x eap enabled
cumulus@switch:~$ nv config apply
When you enable or disable 802.1X on an interface, hostapd reloads; however, existing authorized sessions do not reset.
Edit the /etc/hostapd.conf file to configure 802.1X settings, then restart the hostapd service.
The following example:
- Sets the 802.1X RADIUS server IP address to 10.10.10.1.
- Sets the 802.1X RADIUS shared secret to mysecret.
- Enables 802.1X on swp1 through swp3.
cumulus@switch:~$ sudo nano /etc/hostapd.conf
...
interfaces=swp1,swp2,swp3
...
auth_server_addr=10.10.10.1
auth_server_port=1812
auth_server_shared_secret=mysecret
...
The following example:
- Sets the 802.1X RADIUS server IP address to 10.10.10.1 and the VRF to BLUE.
- Sets the 802.1X RADIUS shared secret to mysecret.
- Sets the 802.1X RADIUS authentication port to 2813.
- Sets the 802.1X RADIUS accounting port to 2812.
- Sets the fixed IP address for the RADIUS client to receive requests to 10.10.10.6.
- Sets the EAP reauthentication interval to 40.
- Enables 802.1X on swp1 through swp3.
cumulus@switch:~$ sudo nano /etc/hostapd.conf
...
interfaces=swp1,swp2,swp3
...
eap_reauth_period=40
...
auth_server_addr=10.10.10.1%BLUE
auth_server_port=1813
auth_server_shared_secret=mysecret
acct_server_addr=10.10.10.1%BLUE
acct_server_port=2812
acct_server_shared_secret=mysecret
radius_client_addr=10.10.10.6
...
Enable then restart the hostapd service:
cumulus@switch:~$ sudo systemctl enable hostapd
cumulus@switch:~$ sudo systemctl restart hostapd
NVIDIA recommends you set the following configuration in the /etc/network/interfaces file for the 802.1X enabled interfaces:
...
auto swp1
iface swp1
bridge-access <vlan>
bridge-learning off
mstpctl-bpduguard yes
mstpctl-portadminedge yes
auto swp2
iface swp2
bridge-access <vlan>
bridge-learning off
mstpctl-bpduguard yes
mstpctl-portadminedge yes
auto swp3
iface swp3
bridge-access <vlan>
bridge-learning off
mstpctl-bpduguard yes
mstpctl-portadminedge yes
MAC-based Authentication
MAC-based authentication (MBA) enables bridged interfaces to allow devices to bypass authentication based on their MAC address. This is useful for devices that do not support EAP, such as printers or phones.
You must configure MBA on both the RADIUS server and the RADIUS client (the Cumulus Linux switch).
Changing the MBA settings does not reset existing authorized user ports. However, changing the MBA activation delay restarts hostapd, which forces existing, authorized users to reauthenticate.
To configure MBA:
Enable MBA in a bridged interface. The following example enables MBA on swp1:
cumulus@switch:~$ nv set interface swp1 dot1x mba enabled
cumulus@switch:~$ nv config apply
Edit the /etc/hostapd.conf file. The following example enables MBA on swp1.
cumulus@switch:~$ sudo nano hostapd.conf
...
mab_interfaces=swp1
...
Restart the hostapd service:
cumulus@switch:~$ sudo systemctl restart hostapd
Auth-fail VLAN
If a non-authorized supplicant tries to communicate with the switch, you can route traffic from that device to a different VLAN and associate that VLAN with one of the switch ports to which the supplicant attaches. Cumulus Linux assigns the auth-fail VLAN by manipulating the PVID of the interface.
Changing the auth-fail VLAN settings does not reset existing authorized user ports. However, changing the auth-fail VLAN ID restarts hostapd, which forces existing, authorized users to reauthenticate.
The following example sets the auth-fail VLAN ID to 777 and enables auth-fail VLAN on swp1.
cumulus@switch:~$ nv set system dot1x auth-fail-vlan 777
cumulus@switch:~$ nv set interface swp1 dot1x auth-fail-vlan enabled
cumulus@switch:~$ nv config apply
If the authentication for swp1 fails, the interface moves to the auth-fail VLAN:
cumulus@switch:~$ nv show interface swp1 dot1x
Interface MAC Address Attribute Value
--------- ----------------- ---------------------------- -----------------
swp1 00:02:00:00:00:08 Status Flags [PARKED_VLAN]
Username vlan60
Authentication Type MD5
VLAN 777
Session Time (seconds) 24772
EAPOL Frames RX 9
EAPOL Frames TX 12
EAPOL Start Frames RX 1
EAPOL Logoff Frames RX 0
EAPOL Response ID Frames RX 4
EAPOL Response Frames RX 8
EAPOL Request ID Frames TX 4
EAPOL Request Frames TX 8
EAPOL Invalid Frames RX 0
EAPOL Length Error Frames Rx 0
EAPOL Frame Version 2
EAPOL Auth Last Frame Source 00:02:00:00:00:08
EAPOL Auth Backend Responses 8
RADIUS Auth Session ID C2FED91A39D8D605
Edit the /etc/hostapd.conf file to add the auth-fail VLAN ID and interface:
cumulus@switch:~$ sudo nano hostapd.conf
...
parking_vlan_interfaces=swp1
parking_vlan_id=777
...
Restart the hostapd service:
cumulus@switch:~$ sudo systemctl restart hostapd
If the authentication for swp1 fails, the interface moves to the auth-fail VLAN.
Dynamic VLAN Assignments
A common requirement for campus networks is to assign dynamic VLANs to specific users in combination with IEEE 802.1x. After authenticating a supplicant, the user is assigned a VLAN based on the RADIUS configuration. Cumulus Linux assigns the dynamic VLAN by manipulating the PVID of the interface.
To enable dynamic VLAN assignment globally, where VLAN attributes from the RADIUS server apply to the bridge:
Run the nv set system dot1x dynamic-vlan optional or nv set system dot1x dynamic-vlan required command. If you run the nv set system dot1x dynamic-vlan required command, when VLAN attributes do not exist in the access response packet from the RADIUS server, the user is not authorized and has no connectivity. If the RADIUS server returns VLAN attributes but the user has an incorrect password, the user goes in the auth-fail VLAN (if you configure auth-fail VLAN).
cumulus@switch:~$ nv set system dot1x dynamic-vlan optional
cumulus@switch:~$ nv config apply
cumulus@switch:~$ nv set system dot1x dynamic-vlan required
cumulus@switch:~$ nv config apply
The following example shows a typical RADIUS configuration (shown for FreeRADIUS,) for a user with dynamic VLAN assignment:
# # VLAN 100 Client Configuration for Freeradius RADIUS Server.
# # This is not part of the CL configuration.
vlan10client Cleartext-Password := "client1password"
Service-Type = Framed-User,
Tunnel-Type = VLAN,
Tunnel-Medium-Type = "IEEE-802",
Tunnel-Private-Group-ID = 100
Verify the configuration (notice the [AUTHORIZED] status in the output):
cumulus@switch:~$ nv show interface dot1x-summary
Interface MAC Address Attribute Value
--------- ----------------- ---------------------------- --------------------------
swp1 00:02:00:00:00:08 Status Flags [DYNAMIC_VLAN][AUTHORIZED]
Username host1
Authentication Type MD5
VLAN 888
Session Time (seconds) 799
EAPOL Frames RX 3
EAPOL Frames TX 3
EAPOL Start Frames RX 1
EAPOL Logoff Frames RX 0
EAPOL Response ID Frames RX 1
EAPOL Response Frames RX 2
EAPOL Request ID Frames TX 1
EAPOL Request Frames TX 2
EAPOL Invalid Frames RX 0
EAPOL Length Error Frames Rx 0
EAPOL Frame Version 2
EAPOL Auth Last Frame Source 00:02:00:00:00:08
EAPOL Auth Backend Responses 2
RADIUS Auth Session ID 939B1A53B624FC56
Edit the
/etc/hostapd.conffile to set thedynamic_vlanoption.- Specify 1 for VLAN attributes to be optional.
- Specify 2 to require VLAN attributes; if VLAN attributes do not exist in the access response packet returned from the RADIUS server, the user is not authorized and has no connectivity. If the RADIUS server returns VLAN attributes but the user has an incorrect password, the user goes in the auth-fail VLAN, if you have configured auth-fail VLAN.
cumulus@switch:~$ sudo nano /etc/hostapd.conf ... dynamic_vlan=1 ...Remove the
eap_send_identity=0option.Restart the
hostapdservice:cumulus@switch:~$ sudo systemctl restart hostapd
The following example shows a typical RADIUS configuration (shown for FreeRADIUS, not typically configured or run on the Cumulus Linux device) for a user with a dynamic VLAN assignment:
# # VLAN 100 Client Configuration for Freeradius RADIUS Server.
# # This is not part of the CL configuration.
vlan10client Cleartext-Password := "client1password"
Service-Type = Framed-User,
Tunnel-Type = VLAN,
Tunnel-Medium-Type = "IEEE-802",
Tunnel-Private-Group-ID = 100
To disable dynamic VLAN assignment, where the Cumulus Linux ignores VLAN attributes sent from the RADIUS server and users authenticate based on existing credentials:
cumulus@switch:~$ nv set system dot1x dynamic-vlan disabled
cumulus@switch:~$ nv config apply
/etc/hostapd.conf file to set the eap_send_identity option to 0, then restart the hostapd service with the sudo systemctl restart hostapd command.Enabling or disabling dynamic VLAN assignment restarts hostapd, which forces existing, authorized users to reauthenticate.
MAC Addresses per Port
You can specify the maximum number of authenticated MAC addresses allowed on an interface. You can specify any number between 0 and 255. The default value is 6.
The following example sets the maximum number of authenticated MAC addresses to 10.
cumulus@switch:~$ nv set system dot1x max-stations 10
cumulus@switch:~$ nv config apply
Edit the /etc/hostapd.conf file to add the max_num_sta= option. For example:
cumulus@switch:~$ sudo nano /etc/hostapd.conf
eap_server=0
ieee8021x=1
driver=wired
dynamic_vlan=1
max_num_sta=10
...
Restart the hostapd service :
cumulus@switch:~$ sudo systemctl restart hostapd
Host Modes
Cumulus Linux provides the following 802.1X host modes:
- Multi host authenticated mode, where RADIUS must authorize each supplicant to send traffic through the 802.1X interface. This is the default mode.
- Multi host mode, where the interface remains closed for all traffic until RADIUS authorizes the first supplicant. After authorization, any host can send and receive traffic through the 802.1X interface as long as the supplicant remains authorized.
Multi Host Mode and MBA
When you enable multi host mode on an 802.1X interface with MBA, the first authorized supplicant does not need to run an EAP client but authorizes according to its MAC address.
Multi Host Mode and Auth-fail VLAN
When you enable multi host mode on an 802.1X interface with auth-fail VLAN, when the first supplicant fails to authorize, Cumulus Linux changes the access VLAN on the interface to auth-fail-vlan. The port does not allow traffic from other MAC addresses.
Multi Host Mode and Port Security
Port security limits port access to a specific number of MAC addresses or specific MAC addresses so that the port does not forward ingress traffic from undefined source addresses.
If you enable port security and 802.1X multi host mode on an interface, the MAC address limit that port security enforces on the interface limits the number of traffic sources after authorization.
In multi host mode, Cumulus Linux adds the authorized supplicant MAC address as a static sticky MAC in the forwarding table. The MAC address limit that port security enforces does not account for the supplicant MAC. For example, when you set the port security MAC limit to 2 on an interface, the supplicant and two more hosts can send traffic through the interface.
If you enable 802.1X after the switch learns port security MAC addresses, Cumulus Linux deletes the dynamic MAC addresses installed with port security from the forwarding table. Cumulus Linux disables bridge learning on an interface with 802.1X configuration; therefore, port security applies only after RADIUS authorizes the first supplicant.
Configure the Host Mode
To configure the host mode on an 802.1X interface:
The following example sets multi host mode on swp1:
cumulus@switch:~$ nv set interface swp1 dot1x host-mode multi-host
cumulus@switch:~$ nv config apply
The following example changes host mode back to the default setting (multi host authenticated) on swp1:
cumulus@switch:~$ nv set interface swp1 dot1x host-mode multi-host-authenticated
cumulus@switch:~$ nv config apply
To change back to the default host mode, you can also run the nv unset interface <interface> dot1x host-mode command.
Edit the /etc/hostapd.conf file to set the multihost_interfaces option to the 802.1X interface on which you want to enable multi host mode, then restart the hostapd service.
The following example configures multi host mode on swp1:
cumulus@switch:~$ sudo nano /etc/hostapd.conf
...
ap_server=0
ieee8021x=1
driver=wired
dynamic_vlan=0
eap_send_identity=
interfaces=swp1,swp2,swp3
voice_interfaces=
mab_interfaces=
dynamic_acl_interfaces=
default_dynamic_acl=default_preauth_dacl.rules
parking_vlan_interfaces=
parking_vlan_id=
multihost_interfaces=swp1
cumulus@switch:~$ sudo systemctl restart hostapd
To change host mode back to the default setting (multi host authenticated), remove the interface from the multihost_interfaces line in the /etc/hostapd.conf file, then restart the hostapd service.
cumulus@switch:~$ sudo nano /etc/hostapd.conf
...
...
mab_interfaces=
dynamic_acl_interfaces=
default_dynamic_acl=default_preauth_dacl.rules
parking_vlan_interfaces=
parking_vlan_id=
multihost_interfaces=
cumulus@switch:~$ sudo systemctl restart hostapd
When you change the mode on an 802.1X interface from multi host authentication (with multiple authorized supplicants) to multi host, Cumulus Linux brings down all existing sessions and closes down the port until one of the supplicants authenticates successfully.
When you change the mode on an 802.1X interface from multi host to multi host authentication, Cumulus Linux brings down existing sessions and disables bridge learning.
Show the Current Host Mode
To show the current host mode, run the nv show interface <interface> dot1x command:
cumulus@switch:~$ nv show interface swp1 dot1x
operational applied
--------- ----------- ----------
eap enabled
host-mode multi-host
...
Deauthenticate an 802.1x Supplicant
To deauthenticate an 802.1X supplicant on an interface, run the nv action deauthenticate interface <interface> dot1x authorized-sessions <mac-address> command:
cumulus@switch:~$ nv action deauthenticate interface swp1 dot1x authorized-sessions 00:55:00:00:00:09
If you do not want to notify the supplicant of the deauthentication, you can add the silent option:
cumulus@switch:~$ nv action deauthenticate interface swp1 dot1x authorized-sessions 00:55:00:00:00:09 silent
Troubleshooting
Check Connectivity Between Supplicants
To check connectivity between two supplicants, ping one host from the other:
root@host1:/home/cumulus# ping 198.51.100.2
PING 10.0.0.2 (10.0.0.2) 56(84) bytes of data.
64 bytes from 10.0.0.2: icmp_seq=1 ttl=64 time=0.604 ms
64 bytes from 10.0.0.2: icmp_seq=2 ttl=64 time=0.552 ms
^C
--- 10.0.0.2 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1000ms
rtt min/avg/max/mdev = 0.552/0.578/0
Show RADIUS Server Configuration
To show the list of RADIUS servers, run the nv show system dot1x radius command:
cumulus@switch:~$ nv show system dot1x radius
operational applied
-------- ----------- ---------
[server] 10.10.10.1
To show configuration information for RADIUS servers, run the nv show system dot1x radius server command:
cumulus@switch:~$ nv show system dot1x radius server
Server accounting-port authentication-port priority shared-secret vrf
--------- --------------- ------------------- -------- ------------- ---
10.10.10.1 1813 1812 1
To show configuration information for a specific RADIUS server, run the nv show system dot1x radius server <ip-address> command:
cumulus@switch:~$ nv show system dot1x radius server 10.10.10.1
operational applied
------------------- ----------- -------
priority 1 1
accounting-port 1813 1813
authentication-port 1812 1812
shared-secret *
Show 802.1X Configuration and Authorization Information
To check which MAC addresses RADIUS has authorized, run the nv show interface --view=dot1x-summary command:
cumulus@switch:~$ nv show interface --view=dot1x-summary
Interface Mac-Address Status Auth-Type Username Vlan Session-id
--------- ----------------- ---------- --------- ------------ ---- ----------------
eth0 00:55:00:00:00:09 AUTHORIZED MBA 005500000009 10 946E00ED478CC8D3
00:02:00:00:00:09 AUTHORIZED MD5 vlan10 10 9EA1784C12F4E646
lo 00:55:00:00:00:09 AUTHORIZED MBA 005500000009 10 946E00ED478CC8D3
00:02:00:00:00:09 AUTHORIZED MD5 vlan10 10 9EA1784C12F4E646
mgmt 00:55:00:00:00:09 AUTHORIZED MBA 005500000009 10 946E00ED478CC8D3
00:02:00:00:00:09 AUTHORIZED MD5 vlan10 10 9EA1784C12F4E646
swp1 00:55:00:00:00:09 AUTHORIZED MBA 005500000009 10 946E00ED478CC8D3
00:02:00:00:00:09 AUTHORIZED MD5 vlan10 10 9EA1784C12F4E646
swp2 00:55:00:00:00:09 AUTHORIZED MBA 005500000009 10 946E00ED478CC8D3
00:02:00:00:00:09 AUTHORIZED MD5 vlan10 10 9EA1784C12F4E646
swp3 00:55:00:00:00:09 AUTHORIZED MBA 005500000009 10 946E00ED478CC8D3
00:02:00:00:00:09 AUTHORIZED MD5 vlan10 10 9EA1784C12F4E646
swp4 00:55:00:00:00:09 AUTHORIZED MBA 005500000009 10 946E00ED478CC8D3
00:02:00:00:00:09 AUTHORIZED MD5 vlan10 10 9EA1784C12F4E646
swp5 00:55:00:00:00:09 AUTHORIZED MBA 005500000009 10 946E00ED478CC8D3
00:02:00:00:00:09 AUTHORIZED MD5 vlan10 10 9EA1784C12F4E646
swp6 00:55:00:00:00:09 AUTHORIZED MBA 005500000009 10 946E00ED478CC8D3
00:02:00:00:00:09 AUTHORIZED MD5 vlan10 10 9EA1784C12F4E646
To show 802.1X configuration settings and authenticated session information for an interface, run the nv show interface <interface> dot1x command:
cumulus@switch:~$ nv show interface swp1 dot1x
operational applied
-------------- ----------- --------
eap enabled
mba disabled
auth-fail-vlan disabled
Authenticated Sessions
=========================
Mac Auth-Type Session-id Status Username Vlan Eapol TX Eapol RX Err RX Req TX Resp RX Start RX Req-id TX Resp-id RX Invalid RX Logoff RX
----------------- --------- ---------------- ---------- ------------ ---- -------- -------- ------ ------ ------- -------- --------- ---------- ---------- ---------
00:02:00:00:00:09 MD5 9EA1784C12F4E646 AUTHORIZED vlan10 10 3 3 0 2 2 1 1 1 0 0
00:55:00:00:00:09 MBA 946E00ED478CC8D3 AUTHORIZED 005500000009 10 0 3 0 0 0 0 0 0 0 0
To show the authenticated sessions and statistics for an interface, run the nv show interface <interface> dot1x authenticated-sessions command:
cumulus@switch:~$ nv show interface swp1 dot1x authenticated-sessions
Mac Auth-Type Session-id Status Username Vlan Eapol TX Eapol RX Err RX Req TX Resp RX Start RX Req-id TX Resp-id RX Invalid RX Logoff RX
----------------- --------- ---------------- ---------- ------------ ---- -------- -------- ------ ------ ------- -------- --------- ---------- ---------- ---------
00:02:00:00:00:09 MD5 9EA1784C12F4E646 AUTHORIZED vlan10 10 3 3 0 2 2 1 1 1 0 0
00:55:00:00:00:09 MBA 946E00ED478CC8D3 AUTHORIZED 005500000009 10 0 3 0 0 0 0 0 0 0 0
To show the authenticated sessions and statistics for a specific MAC address, run the nv show interface <interface-id> dot1x authenticated-sessions <mac-address> command:
cumulus@switch:~$ nv show interface swp1 dot1x authenticated-sessions 00:02:00:00:00:09
operational
------------------------- -----------------
username vlan10
auth-type MD5
status AUTHORIZED
vlan 10
mac-address 00:02:00:00:00:09
session-id 9EA1784C12F4E646
counters
eapol-frames-tx 3
eapol-frames-rx 3
eapol-len-err-frames-rx 0
eapol-req-frames-tx 2
eapol-resp-frames-rx 2
eapol-start-frames-rx 1
eapol-req-id-frames-tx 1
eapol-resp-id-frames-rx 1
eapol-invalid-frames-rx 0
eapol-logoff-frames-rx 0
Show 802.1X Statistics
To check statistics for all interfaces, run the nv show interface --view=dot1x-counters command:
cumulus@switch:~$ nv show interface --view=dot1x-counters
Interface Mac-Address Eapol TX Eapol RX Req TX Resp RX Err RX Start RX Req-id TX Resp-id RX Invalid RX Logoff RX
--------- ----------------- -------- -------- ------ ------- ------ -------- --------- ---------- ---------- ---------
eth0 00:55:00:00:00:09 0 3 0 0 0 0 0 0 0 0
00:02:00:00:00:09 3 3 2 2 0 1 1 1 0 0
lo 00:55:00:00:00:09 0 3 0 0 0 0 0 0 0 0
00:02:00:00:00:09 3 3 2 2 0 1 1 1 0 0
mgmt 00:55:00:00:00:09 0 3 0 0 0 0 0 0 0 0
00:02:00:00:00:09 3 3 2 2 0 1 1 1 0 0
swp1 00:55:00:00:00:09 0 3 0 0 0 0 0 0 0 0
00:02:00:00:00:09 3 3 2 2 0 1 1 1 0 0
swp2 00:55:00:00:00:09 0 3 0 0 0 0 0 0 0 0
00:02:00:00:00:09 3 3 2 2 0 1 1 1 0 0
swp3 00:55:00:00:00:09 0 3 0 0 0 0 0 0 0 0
00:02:00:00:00:09 3 3 2 2 0 1 1 1 0 0
swp4 00:55:00:00:00:09 0 3 0 0 0 0 0 0 0 0
00:02:00:00:00:09 3 3 2 2 0 1 1 1 0 0
swp5 00:55:00:00:00:09 0 3 0 0 0 0 0 0 0 0
00:02:00:00:00:09 3 3 2 2 0 1 1 1 0 0
swp6 00:55:00:00:00:09 0 3 0 0 0 0 0 0 0 0
00:02:00:00:00:09 3 3 2 2 0 1 1 1
...
Advanced Troubleshooting
You can perform more advanced troubleshooting with the following commands.
To increase the debug level in hostapd, copy over the hostapd service file, then add -d, -dd or -ddd to the ExecStart line in the hostapd.service file:
cumulus@switch:~$ cp /lib/systemd/system/hostapd.service /etc/systemd/system/hostapd.service
cumulus@switch:~$ sudo nano /etc/systemd/system/hostapd.service
...
ExecStart=/usr/sbin/hostapd -ddd -c /etc/hostapd.conf
...
To watch debugs with journalctl as supplicants attempt to connect:
cumulus@switch:~$ sudo journalctl -n 1000 -u hostapd # see the last 1000 lines of hostapd debug logging
cumulus@switch:~$ sudo journalctl -f -u hostapd # continuous tail of the hostapd daemon debug logging
To check ACL rules in /etc/cumulus/acl/policy.d/100_dot1x_swpX.rules before and after a supplicant attempts to authenticate:
cumulus@switch:~$ sudo cl-acltool -L eb | grep swp1
cumulus@switch:~$ sudo cl-netstat | grep swp1 # look at interface counters
To check tc rules in /var/lib/hostapd/acl/tc_swpX.rules with:
cumulus@switch:~$ sudo tc -s filter show dev swp1 parent 1:
cumulus@switch:~$ sudo tc -s filter show dev swp1 parent ffff: