NVIDIA DRIVE AGX Communications and Security Services Developer Guide 5.1.6.0 Release |
NVIDIA DRIVE AGX Communications and Security Services Developer Guide 5.1.6.0 Release |
Type of Detection | Description |
Hard Policy Threats | All threats of this type are blocked by default. However, the system can be configured to allow very specific cases to not be blocked. For example, incoming traffic is blocked unless the source of that traffic was already communicated by a Guest VM to effectively ensure an incoming packet filter of unsolicited traffic. However, it is possible to open a specific IP port address to always be open in the configuration file. |
Normal Threat Detection | Different configuration policies can be created depending on the type of threat detected. These policies can include: • No Action • Let Through |
Temporary Threat Detection | Includes attacks that happen for a limited period of time, such as Denial of Service attacks. Includes a mechanism to detect if the attack is still happening. |
Firewall Event | Description |
Scan Okay | Results of firewall scan on the packet are okay. |
Header Frame Error | Flags any error from parsing the header: • MAC frame, IP packet and payload length. • IP header or TCP/UDP/ICMP checksum error. |
IPV6 Frame | Ethernet frame is of type IPV6. |
ARP Frame | Ethernet frame is an ARP frame. |
Frame Type Not Recognized | Filter for ETH frames for which the firewall scan is not available. |
Security Risk | Flag security for these security risks: • Echo request/reply with broadcast frames. • Echo request/reply with multicast frames. • Loopback packets, source MAC|IP, matching destination MAC|IP. • Packet from or to a Guest VM with forged IP. |
No Tracking Entry Match | Filter TCP untracked packets. |
Out of Resources | Flag the out of tracking resources for the TCP/ICMP/UDP packets. |
Source Blocked | Filter for packets with a blacklisted IP, source or destination. |
IP Protocol Not Recognized | Filter for packet using a protocol other than: • IPV4 • PIM internal multicast • UDP • TCP • ICMP |
Port Closed | Filter for packets using non-opened ports. |
Blacklist Request | Flag a peer that has repeatedly sent packets that are not allowed for a configurable number of times. Default is 20. |
TCP Connection Error | Flag any TCP state error during establishment. |
TCP Connection Timeout | Flag timeout on half-opened, default 20 seconds, or established connection, default 2 hours. |
Broadcast Frame | Ethernet frame is a broadcast frame. |
Multicast Frame | Ethernet frame is a multicast frame. |
DHCP Packet | Packet is a DHCP Packet. |
ICMP Fragment | Ping message. |
UDP Fragment | Packet is a UDP Packet. |
UDP Zero Checksum | Bypass checksum on UDP with zero sum. |
DoS Attack Okay | No DoS attack detected. |
DoS Internal Attack L1 | Detected DoS attack from internal source, Level 1. |
DoS External Attack L1 | Detected DoS attack from external source, Level 1. |
DoS Internal Attack L2 | Detected DoS attack from internal source, Level 2. |
DoS External Attack L2 | Detected DoS attack from external source, Level 2. |
DoS Internal Attack L3 | Detected DoS attack from internal source, Level 3. |
DoS External Attack L3 | Detected DoS attack from external source, Level 3. |
Policy Action | Description |
Event Log | All these events are logged for later analysis. |
Event Block | Block the frame if these events occur. |
Event Close Connection | Close connection associated to the current TCP packet. |
Event Close All Connections | Close all TCP connections with timeout. |
Event Blacklist | Request for IP or MAC address to be blacklisted. |
Event Reset | Request for system reset, for future use. |
Event Alert | Request for system alert, for future use. |
Event DoS QOS | Enable QoS on DoS detection. |
Event DoS Blacklist Inbound | Blacklist requests in case of DoS attack, for future use. |
Event DoS Blacklist Outbound | Blacklist requests in case of DoS attack, for future use. |
Policy Action | Description |
AmOk | Reserved for future use. |
AmIndef | Reserved for future use. |
AmMalic | Reserved for future use. |
Policy Action | Description |
DpiOk | Reserved for future use. |
DpiIndef | Reserved for future use. |
DpiMalic | Reserved for future use. |
Note: | Unless indicated, the default policy action for all scan events is to allow the packet; Event Allow. Anti-malware and IP deep packet inspection scans are not supported in this release. |
Policy Action | Description |
FwEventOk | Indicates results of a CAN firewall scan on the packet are okay. |
Suspicious Frame Length | The CAN frame length is not a standard defined size. The size is not of any CAN, external CAN or CAN-FD frame types. |
Message ID Not Allowed | CAN message ID is not configured to be allowed through the CAN firewall. |
Policy Action | Description |
DpiOk | Indicates results of DPI scan on the CAN frame are okay. |
DpiIndef | Results from the DPI scan cannot be determined. |
DpiMalic | Malicious frame detected during the DPI scan. |
Policy Action | Description |
MsgFreqOk | Reserved for future use. |
MsgFreqIndef | Reserved for future use. |
MsgFreqMalic | Reserved for future use. |
Note: | Unless indicated, the default policy action for all scan events is to allow the packet; Event Allow. |
Note: | The Version Information Page displays the configured defaults. These values are not used in this release. |
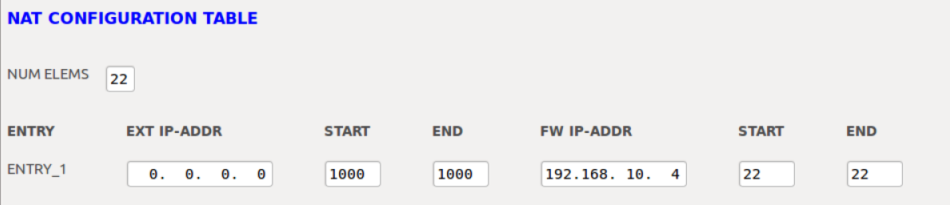
Configuration Value | Description |
Number of Elements | Number of active entries in NAT table. Only this number of entries will be considered on the Comms NAT table, even if the table has more than “Number of Elements” entries in them. |
External IP Address | IP address on Communication Services NIC - 0.0.0.0. |
Port Start | External port on which the connection is made - Start Value. |
Port End | External port on which the connection is made - End Value. |
Firewall IP Address | IP address of the Guest VM that must access the external world. |
Port Start | Internal port on which the connection is made - Start Value. |
Port End | Internal port on which the connection is made - End Value. |
Configuration Values | Description | |
Number of Guests | Reserved for future use. | |
Bandwidth allocation | Total | |
Guest > Host | ||
Guest > Guest | ||
TCP | ||
UDP | ||
ICMP | ||
TCP | Outbound_Ext | |
Inbound_Ext | ||
Internal | ||
Threshold | ||
UDP | Outbound_Ext | |
Inbound_Ext | ||
Internal | ||
Threshold | ||
Slot | Dos_level_0_Escalate | |
Dos_level_0_Wait | ||
Dos_level_1_Escalate | ||
Dos_level_1_Wait | ||
Dos_level_2_Escalate | ||
Dos_level_2_Wait | ||
Dos_level_3_Escalate | ||
Dos_level_3_Wait | ||
Note: | The DoS Configuration Table values in the interface are the default values. Do NOT change these values. |
Configuration Values | Description |
Number of Elements | Number of entries to be configured for this interface. |
Port Start | List of ports allowed through the security firewall - Start Value. |
Port End | List of ports allowed through the security firewall - End Value. |
Enable | Enable/disable the specified ports. |
Note: | These ports are a second line of defense. The NAT Configuration Table must have the correct port forwarding entry defined for that particular interface. |
Configuration Values | Description |
Number of Elements | Number of entries to be configured for this interface. |
Encryption | Encryption options for this IP Address/Port Range. Values include: • Secure - Inspect traffic • Unsecure - Define exceptions • Not set - Entry not used |
IP Address | IP address and mask combination to scan. |
IP Mask | IP address and mask combination to scan. |
Minimum | Port range to scan - Minimum. |
Maximum | Port range to scan - Maximum. |
Configuration Value | Description |
Log Upload time | Time of day at when the logs are uploaded to the log server. |
Log Upload Interval | Number of days before the log gets uploaded to the log server. |
Event Log Count | Counts to reach before logs gets appended to event log. This is to avoid repetitive logging. Consult Security Logging for details. |
Log Timer Interval | The number of hours before the log count is added to eventlog if the Event Log Count is not reached. |
Configuration Value | Description |
PTP Enable/Disable | Enables/Disables the Virtual PTP. |
PTP Arguments | Consult Using PTP Virtualization topic for details. |
Configuration Value | Description |
Server Cipher | Reserved for future use |
Client Cipher | |
Password |