NVIDIA DRIVE AGX Communications and Security Services Developer Guide 5.1.6.0 Release |
NVIDIA DRIVE AGX Communications and Security Services Developer Guide 5.1.6.0 Release |
Component | Description |
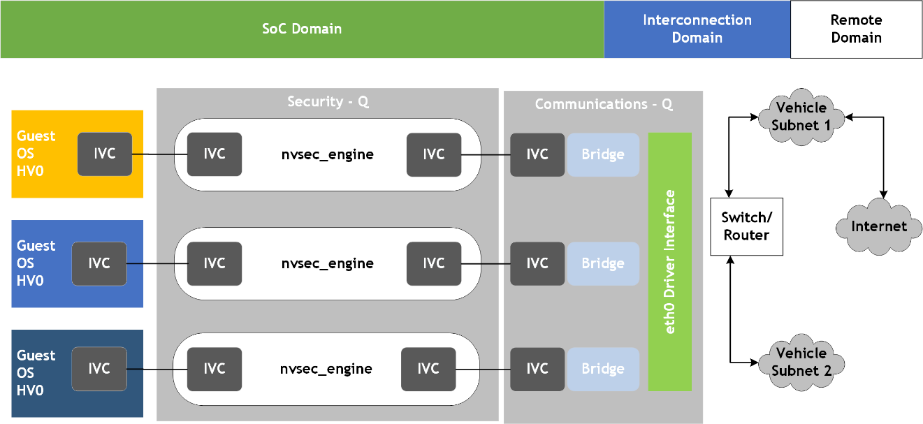
Communications Services | The Communications Service manages the communications of the hardware peripherals. • Guest VMs can access the peripherals as if they were exclusively allocated to that VM. The Communications Service uses the Security Service to manage the routing of traffic to and from the peripherals, and to and from the guest VM. |
Security Services | The Security Service monitors the communications for potential threats and enacts the appropriate policy once a threat is detected. • The guest VM is not aware of the Security Service. • The guest VM has virtualized drivers that appear, to higher layers, like normal hardware drivers. • Multiple guest VMs can access the same peripheral without knowledge of each other. |
Term | Definition |
CAN | Control Area Network |
Comms | Communications Services |
DDOS | Distributed Denial of Service |
DHCP | Dynamic Host Configuration Protocol |
DNS | Domain Name System |
DoS | Denial of Service |
ICMP | Inter Control Message Protocol |
IDPS | Intrusion Detection and Prevention System |
IP | Internet Protocol |
IVC | Inter-Virtual Machine Communication |
MAC | Media Access Control |
NAT | Network Address Translation |
OS | Operating System |
PTP | Precision Time Protocol |
SSL | Secure Sockets Layer |
SoC | System on a Chip |
TCP | Transmit Control Protocol |
TCU | Transmit Control Unit |
TLS | Transport Layer Security |
UDP | User Datagram Protocol |
VLAN | Virtual Local Area Network |
VM | Virtual Machine |