The Configuration Tool
To take advantage of the Communications and Security Services features, configuration parameters must be set to tune the network and security policy settings including:
• Network configuration settings for:
• static or dynamic IP
• Alias IP
• NAT table
• UDP port settings
• Security policy configuration settings for:
• IP, CAN, and AURIX firewall policies
• Denial of Service settings
• IP and MAC blacklist settings
• Port mask settings
These network and security policy configuration settings are generated and stored in a binary file that is usually encrypted and cannot be modified as plain text. The Configuration Tool acts as an interface to read the configuration file and allow for modifications of these settings.
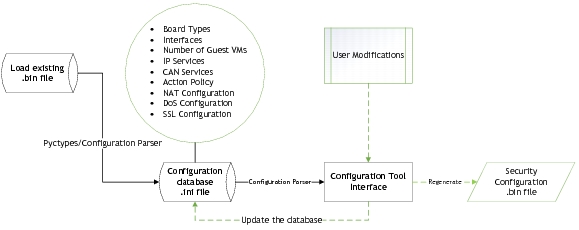
Configuration Tool Process Flow
The configuration tool is a Python-based interface that runs on Linux systems. The tool allows loading of the configuration binary file to modify the settings as required. The configuration tool process flow is as follows:
Use the configuration tool to modify the configuration binary file and save the modified file back to the host system. The configuration binary file can then be updated on the Security Services partition.
Note: | Do NOT edit the generated configuration database .ini file directly. The .ini file can be used to verify existing settings. |
Extracting the Installation Files
The platform includes the configuration binary file and Python scripts required to launch the configuration tool. The SDK Manager interface extracts the configuration file and the Python scripts required to launch the configuration tool in the path:
<PATH_TO_INSTALLATION_FILES>/drive-t186ref-foundation/comms_sec_config/*
• Select the security.config configuration file packaged with the SDK. This configuration file supports the following DRIVE™ AGX system boards
• E3550 Xavier A
• E3550 Xavier B
• P3479 Xavier S
• P2888 Xavier C
Launching the Configuration Tool
To run the configuration tool, the following Python utilities and OpenSSL must be installed on your host Ubuntu system:
• Python (2.x or 3.x versions).
• wxPython (3.0 or above).
• ConfigObj 5.1 Python configuration parser module.
• OpenSSL (to decrypt the configuration file).
If these utilities are not installed, an ImportError is returned when attempting to launch the configuration tool.
Note: | Installing any other version of these utilities, other than the version specified, may cause unexplained behavior. |
To install the Python utilities on the Ubuntu 16.04 or Ubuntu 18.04 host systems
• Execute these commands:
sudo apt-get update (refreshing the repositories)
sudo apt-get install python2.7 (Python 2.7 installation, if not already present)
-Or-
sudo apt install python3 (Python 3 installation, if not already installed)
For Python 2.X versions:
sudo apt-get install python-wxgtk3.0 (Python wx widget)
-Or-
pip install -U wxPython (For the latest wxPython)
sudo pip install configobj (configuration parser for .ini files)
For Python 3.X versions:
sudo apt install python3-pip
pip3 install wxPython
pip3 install configobj
Install any other dependencies that might be prompted during the above steps.
To install OpenSSL and the associated libraries
1. Install the following OpenSSL associated libraries on the host system:
libssl.so
libcrypto.so
These libraries are available in the /usr/lib file path and are required for decrypting the configuration file.
2. Add the path to these libraries to your library path:
LD_LIBRARY_PATH=/usr/lib:$LD_LIBRARY_PATH
If OpenSSL is not installed correctly, an error message is displayed as follows:
ERROR: No encryption library available for decrypt
On Ubuntu 18.04, OpenSSL may already be installed. In this case, link the libraries to enable config file decryption by the config tool:
cd /usr/lib
sudo ln -s x86_64-linux-gnu/libssl3.so libssl.so
sudo ln -s x86_64-linux-gnu/libcrypto.so.1.1 libcrypto.so
To launch the configuration tool
1. Navigate to the Communications and Security configuration file available at:
<PATH_TO_INSTALLATION_FILES>/drive-t186ref-foundation/comms_sec_config
2. Execute the following command to run the Python script.
python -B createConfigSystem.py
This command creates the necessary files for processing the configuration binary file.
3. Launch the config_management_system.py file to view or configure the security and network policies.
The config_management_system.py script is used to configure:
• IP security policies
• Native CAN security policies
• AURIX CAN security policies
• Network IP addresses
• NAT configuration
• Denial of Service parameters
• Blacklist table
• and more
4. Launch the configuration tool by executing the following command:
python Config_Management_System.py -h
usage: Config_Management_System.py [-h] [-i IN_FILE] [-t {0,1,2,3}]
[-s OUT_FILE]
Comms & Security Configuration Tool
optional arguments:
-h, --help show this help message and exit
-i IN_FILE Input file to load
-t {0,1,2,3} Configuration file to edit: 0 = A, 1 = B, 2 = C, 3 = D
-s OUT_FILE Save input file as
python <type_of_config_file.py> -i <path_to_input_binary_file>
5. To launch the GUI for configuring Tegra-A
python Config_Management_System.py -i security.config
-Or-
python Config_Management_System.py -i security.config -t 0
By default, this opens the GUI with Tegra-A settings from the configuration file.
To launch the GUI for configuring Tegra-B:
python Config_Management_System.py -i security.config -t 1
and so on.
6. Optionally, an output filename can be specified to save the configuration to a new file. If an output filename is not provided, the settings are updated in the same file.
For example:
python Network_Config.py -i security.config -s <output_filename>
When launching the Configuration tool, if the following error message is encountered:
Import Error: No module named generated_config_ctypes
It indicates that python -B createConfigSystem.py command has not been executed.
7. To configure relevant security policies individually, execute the desired configuration file.
For example:
IP_Engine_GUI.py
CAN_Engine_GUI.py
Aurix_Engine_GUI.py
Using the Configuration Tool
Use the Configuration tool to perform these security policy updates and network configuration options:
Security Policy Updates |
Policy | Description |
IP_Engine Policies | Used to configure IP security policies for each type of threat or interface. |
Native CAN_Engine Policies | Used to configure native CAN security policies for each type of threat or interface. |
AURIX CAN Engine Policies | Used to set the Ethernet CAN security policies for each type of threat or interface. |
Network Configuration Options |
Option | Description |
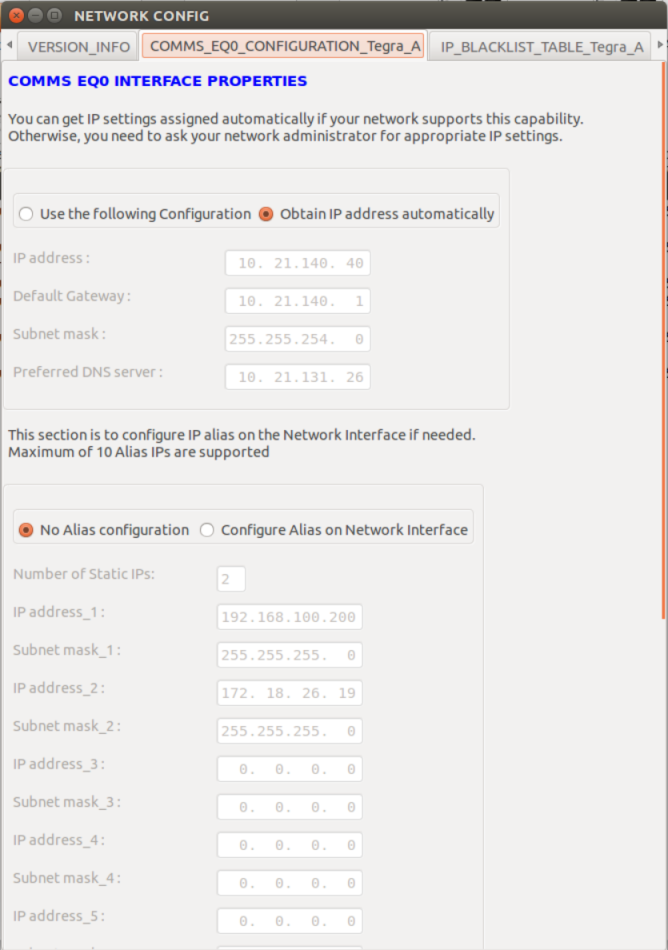
Comms IP Configuration | Used to configure the IP Address and aliases, if needed, on the Communications services network interface. |
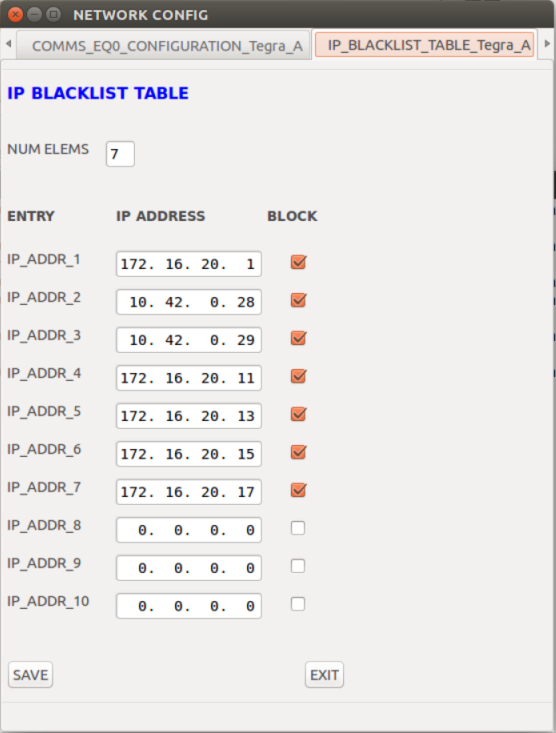
IP Blacklist Table | Firewall setting used to block certain IP Addresses. |
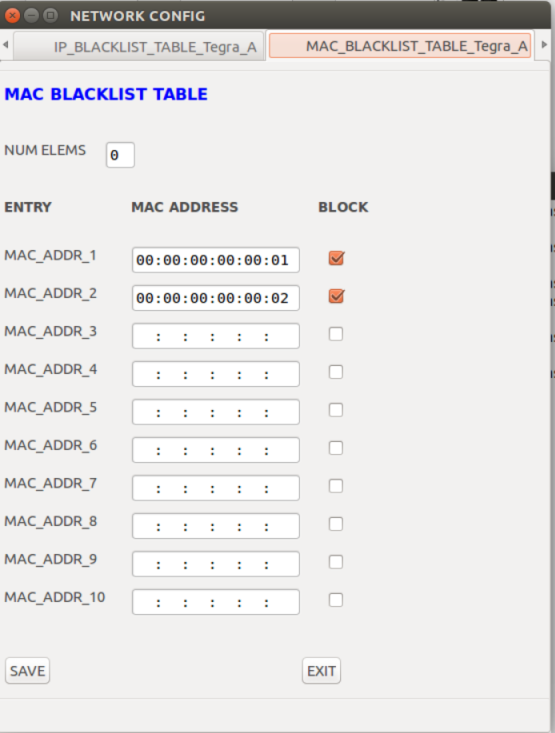
MAC Blacklist Table | Firewall setting used to block certain MAC addresses. |
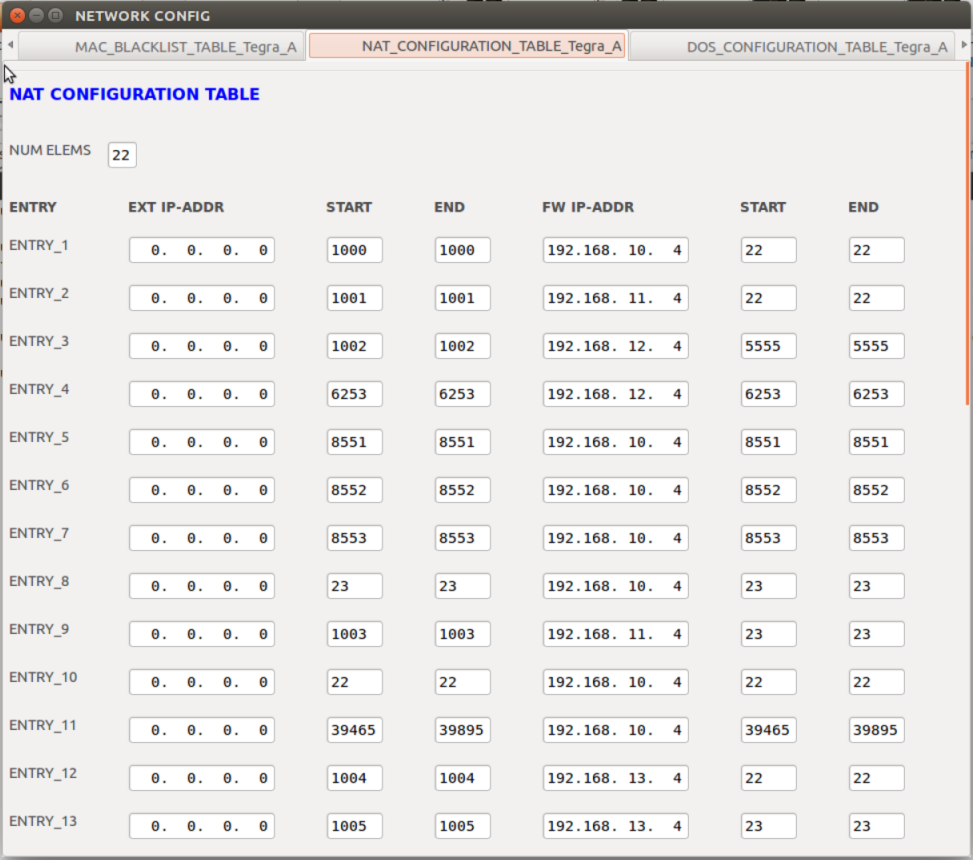
NAT Configuration Table | NAT table on the Communications services used to translate network address information, such as IP address and Port number, between private and public domain. |
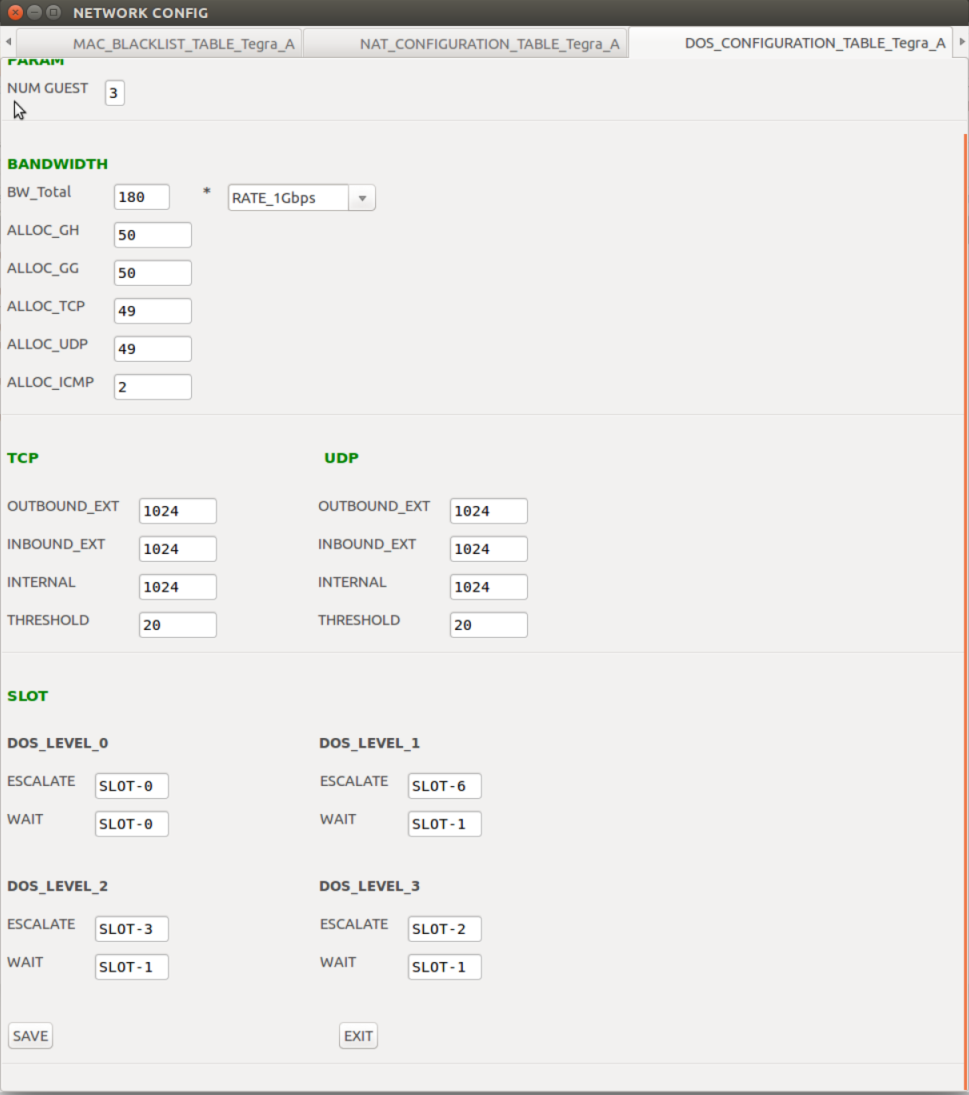
Denial of Service Configuration Table | Configuration values used to determine DoS attacks. |
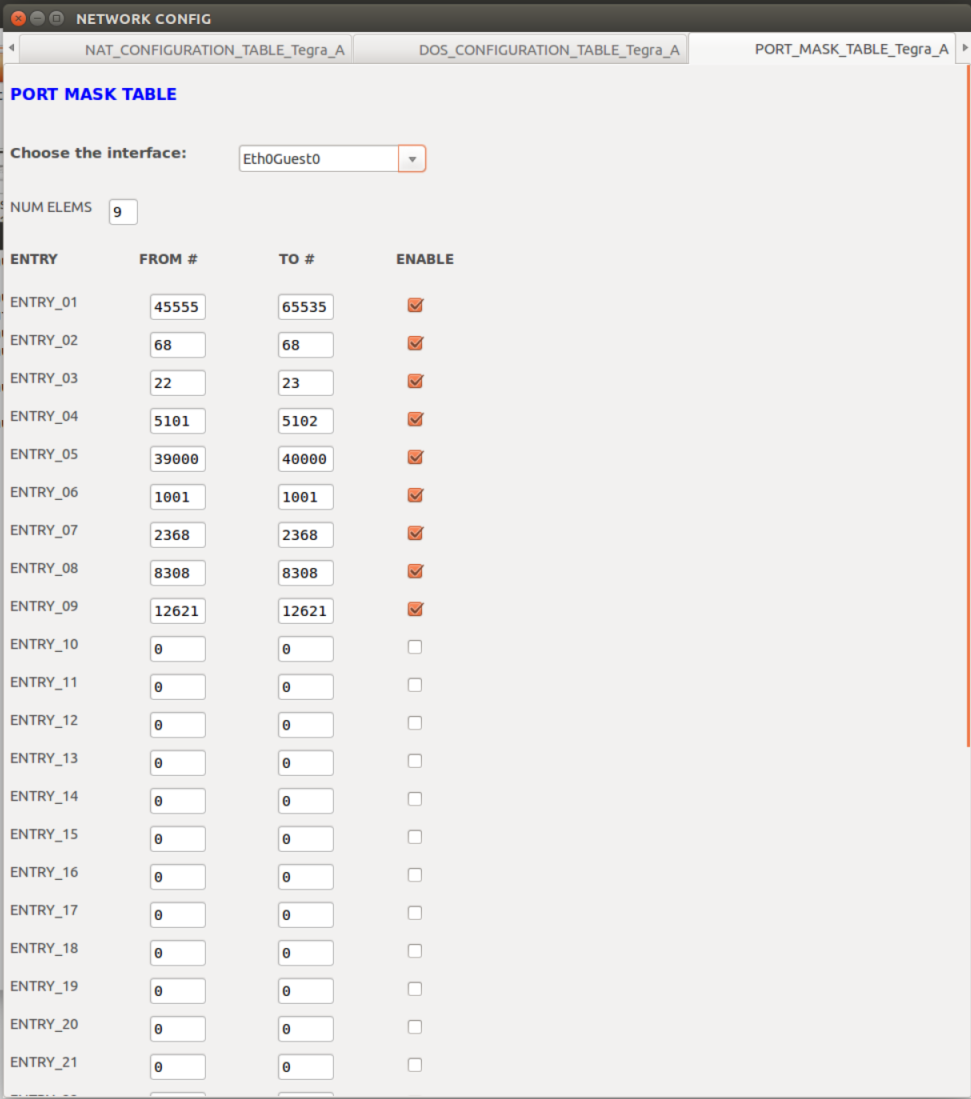
Port Mask Configuration Table | List of ports and interfaces allowed through the security firewall. |
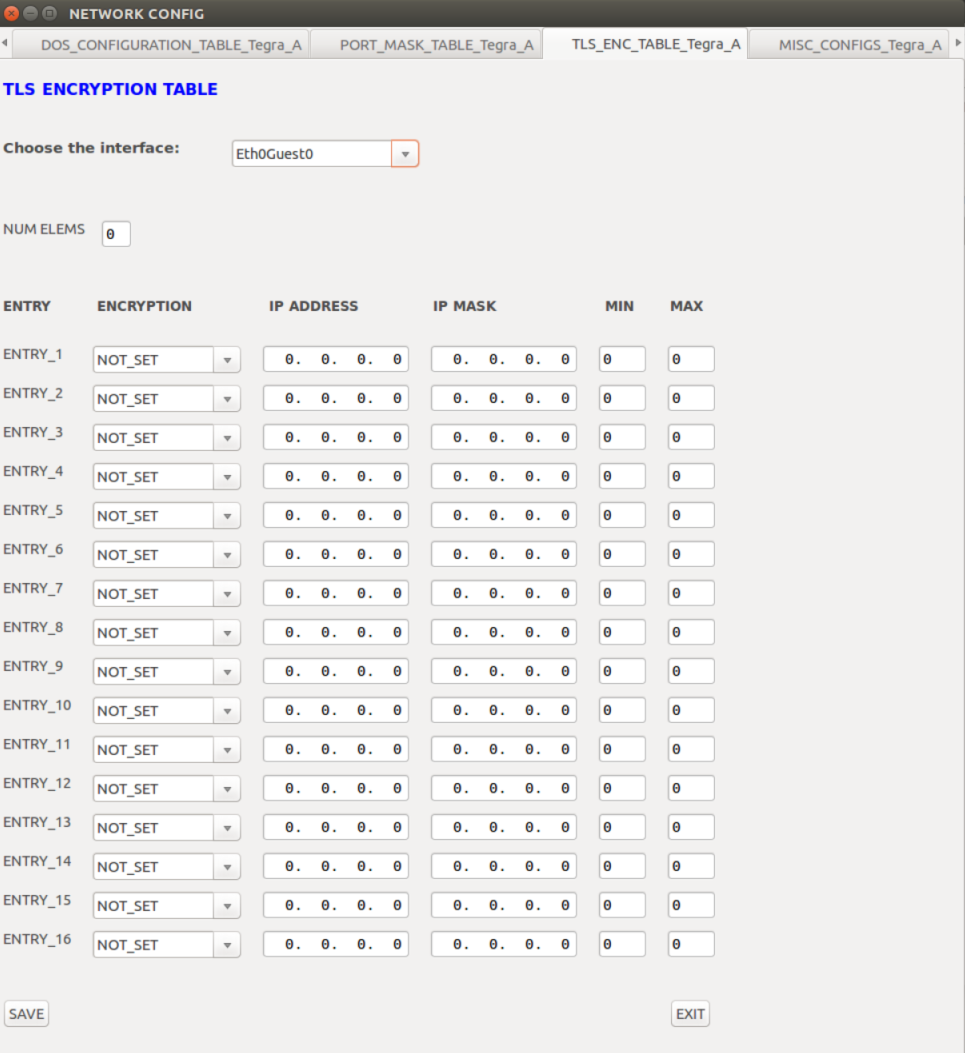
TLS Encryption Table | Transport layer security encryption configuration on a per interface/IP range/Port range basis. |
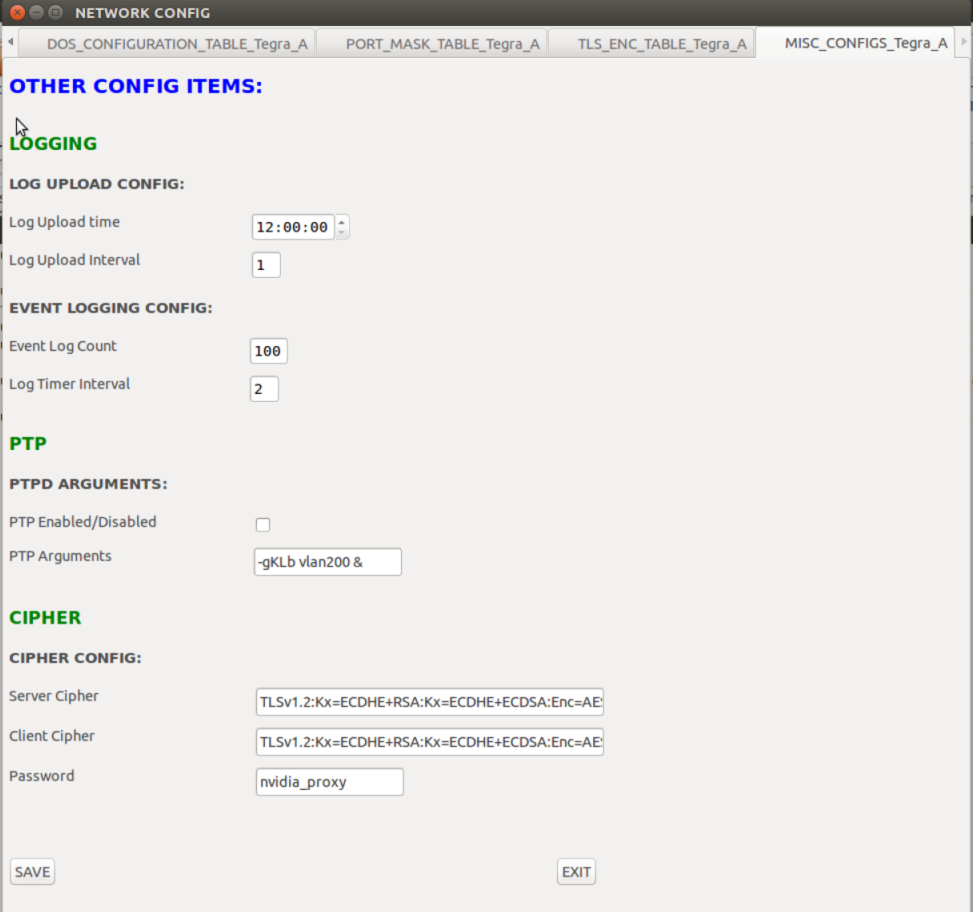
Miscellaneous Config | Configuration options for PTP, logging timer, and cipher keys (read-only). |
Version Control |
Option | Description |
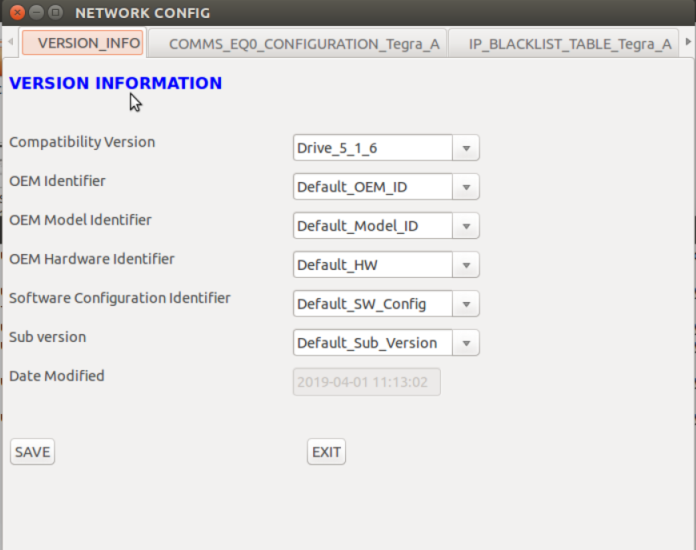
Version Info Table | Used to verify and update the version information of the current configuration file. |
For details on the various configuration options and values, consult <TBD>.
A Tour of the Configuration Tool Interface
The configuration tool interface varies depending on the service being launched.
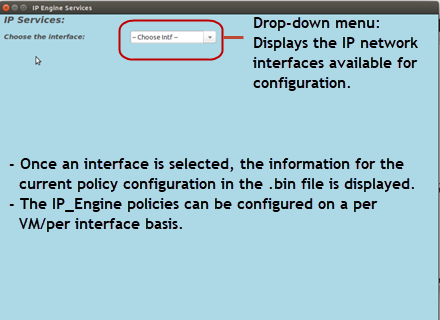
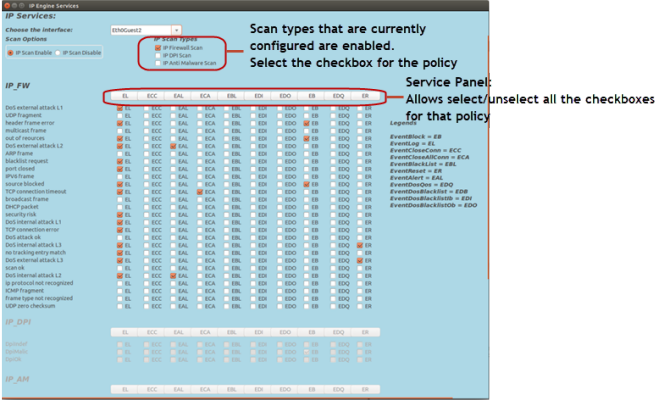
IP Engine Services
When launching the IP_Engine_GUI.py, the interface display is as follows:
• The IP_Engine configuration options are as follows:
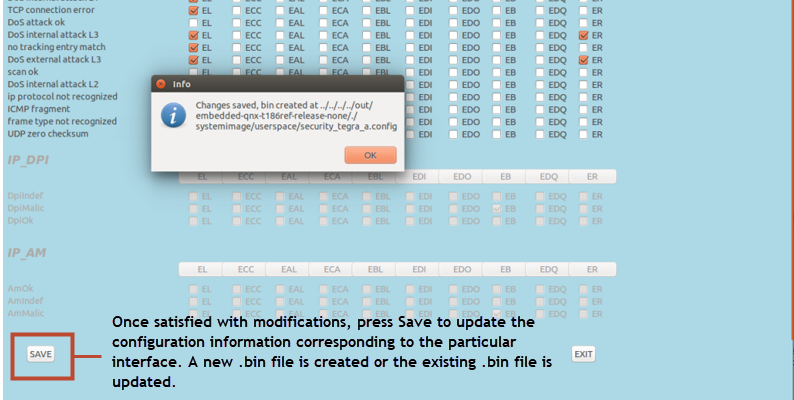
Before navigating to other interfaces, select Save on each interface display for changes to take effect.
CAN Engine Services
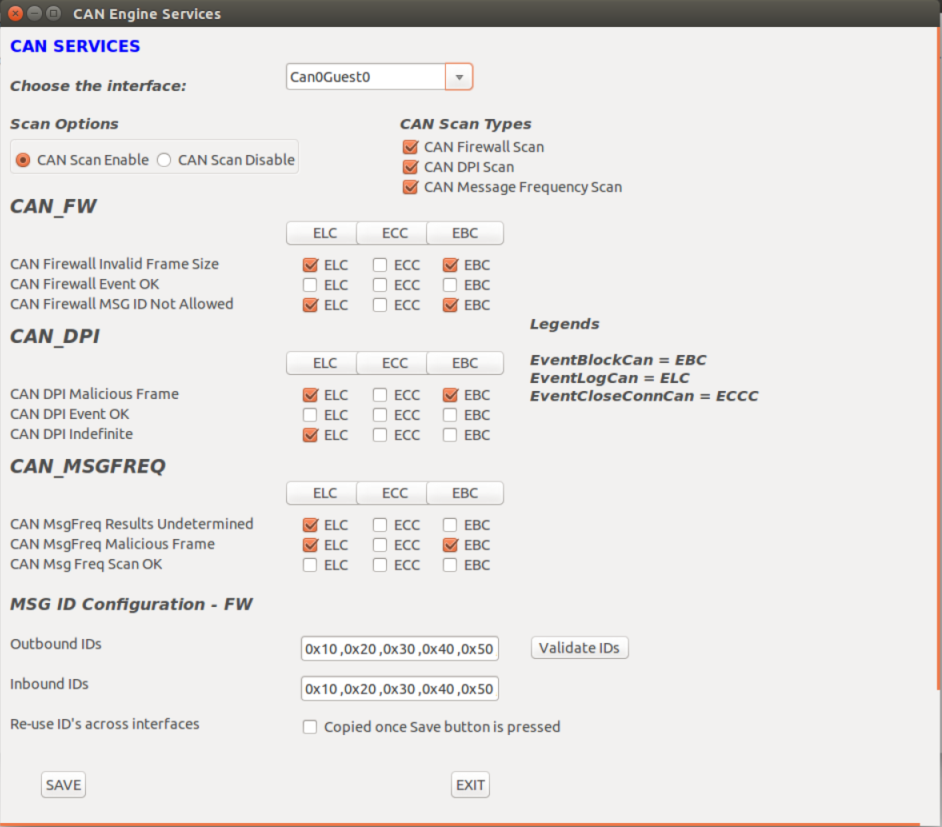
When launching the CAN_Engine_GUI.py, the interface display is as follows:
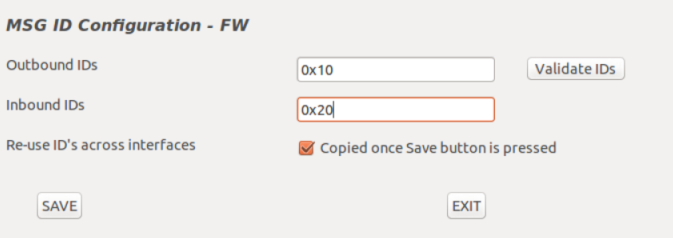
• The CAN Engine service includes an additional option to update the CAN Message IDs for CAN firewall operation.
• The Outbound and Inbound IDs are loaded from the configuration file that corresponds to the Tegra/interface chosen.
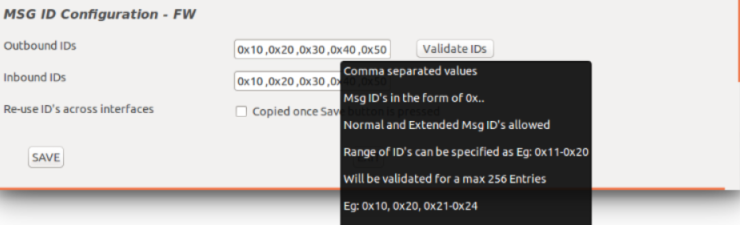
• Hover the mouse over the fields to display the Tooltips to show how the fields are populated.
• Append or modify the IDs in the Inbound or Output fields and update the settings for the Tegra/interface combination.
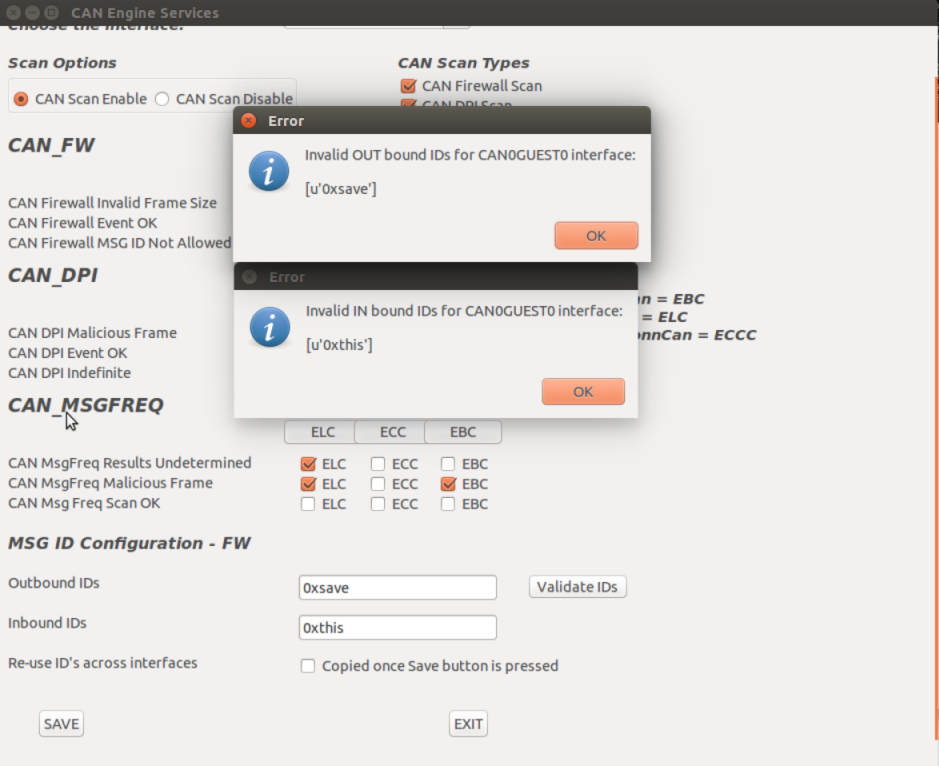
• Use the Validate IDs button to check whether the IDs identified are correct.
• Use the Re-use IDs checkbook to help the user copy over the changes for the ID fields across all other interfaces as displayed in the drop-down menu. The option is available on the main interface, Can0Guest0.
• Select the Save button to save the changes that correspond to the Tegra/interface combination.
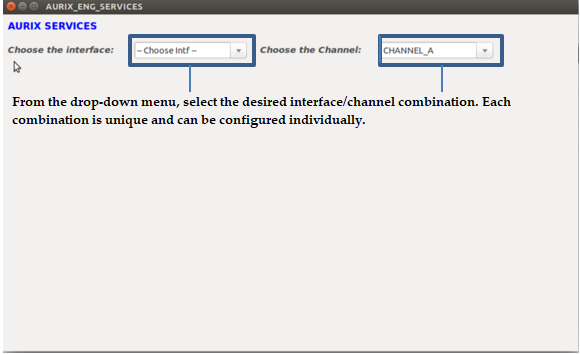
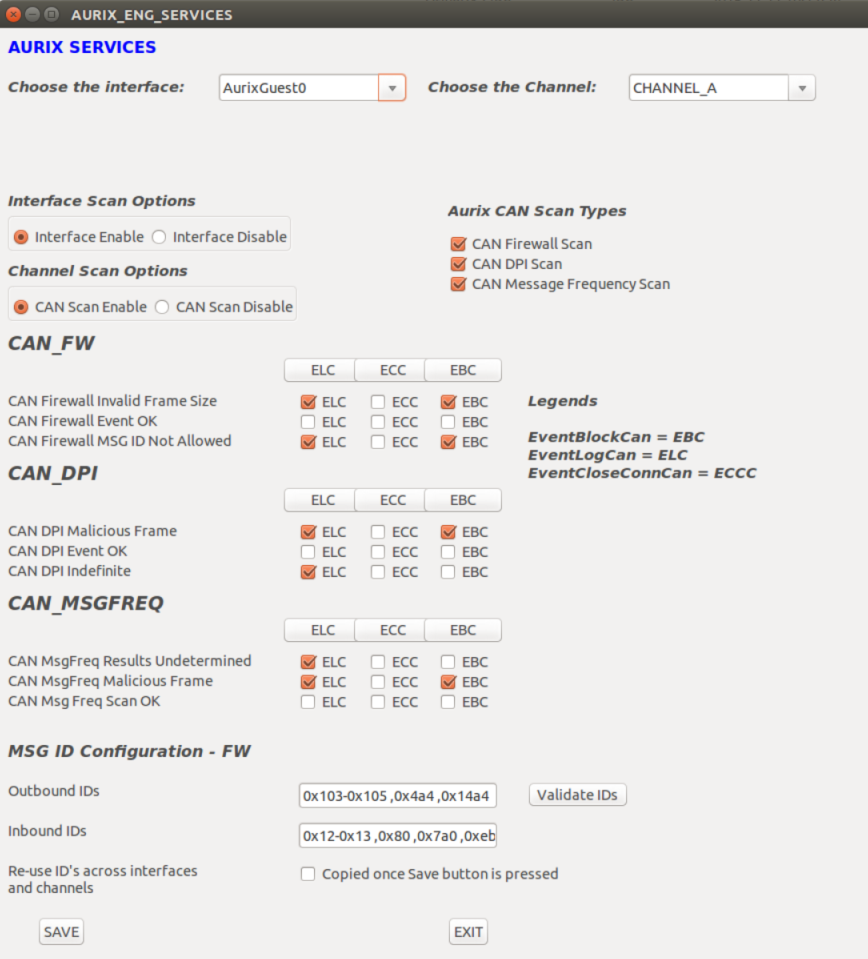
Aurix Engine Services
When launching the Aurix_Engine_GUI.py, the interface display is as follows:
• The Aurix Engine service includes an additional option to update the CAN Message IDs for CAN firewall operation.
• The Outbound and Inbound IDs are loaded from the configuration file that corresponds to the Tegra/channel/interface selected.
• Hover the mouse over the fields to display the Tooltips to show how the fields are populated.
• Append or modify the IDs in the Inbound or Output fields and update the settings for the Tegra/channel/interface combination.
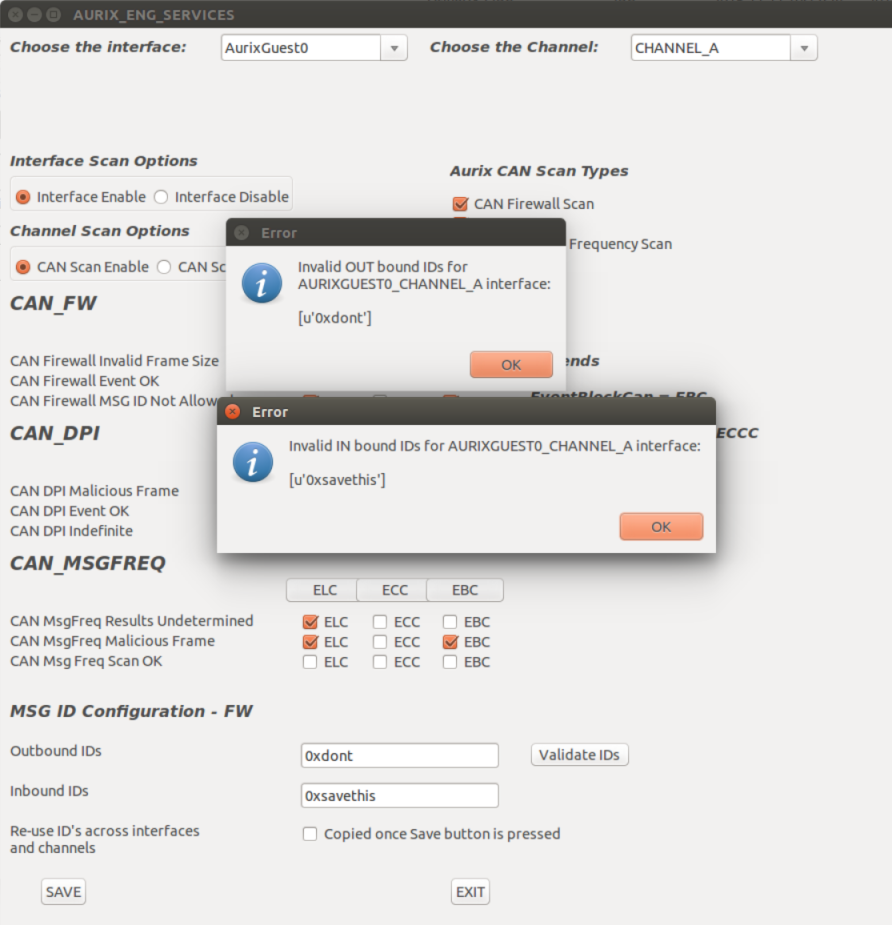
• Use the Validate IDs button to check whether the IDs identified are correct.
• Use the Re-use IDs checkbook to help the user copy over the changes for the ID fields across all other interfaces as displayed in the drop-down menu. The option is available on the main interface, AurixGuest0-Can0Guest0.
• Select the Save button to save the changes that correspond to the Tegra/channel/interface combination.
Network Configuration
When the script python Network_Config.py -i <input_file> is launched, the network configuration options are displayed in the form of tabbed windows. If the -t <tegra> option is not chosen, Tegra-A configuration is loaded by default (also seen on tabbed window in GUI).
IP Configuration |
IP Blacklist Table |
MAC Blacklist Table |
NAT Configuration Table |
DoS Configuration Table |
Port Mask Table |
TLS Encryption Table |
Miscellaneous Configurations
Once satisfied with the configuration modifications, reload the configuration file to the interface to confirm that the modifications have taken effect.
Proceed to update the new configuration to the security partition.
Version Information
The version information display is as follows:
Flashing the Configuration File on the Target
The new configuration file can be updated on the target by the OTA method specified at
Over the Air Update of Security Files.