Linux-based Disk Encryption
Disk encryption ensures that files are always stored on disk in an encrypted form. The files become available to the operating system and applications in readable form while the system is running and unlocked by a trusted user. An unauthorized user inspecting the contents of the disk directly finds garbled random-looking data instead of the actual files.
With user data encryption enabled, the /home directory in the file system is encrypted and user data is available when the system is running. The user /home partition is mounted on a separate disk partition and block level encryption is enabled for that disk.
The NVIDIA implementation uses the dm-crypt kernel module, which is the standard device-mapper interface for encryption functionality provided by the Linux kernel. It is inserted between the disk driver and the file system to transparently encrypt and decrypt the data blocks.
Consult the Linux documentation on dm-crypt at:
The management of dm-crypt is performed with the cryptsetup user-space utility.
Cryptsetup
The
cryptsetup utility sets up disk encryption based on the
DMCrypt kernel module. The NVIDIA implementation sets up the encrypted data disk as a Linux Unified Key Setup (LUKS) partition and configures it with a random passphrase.
Consult the Linux documentation on cryptsetup at:
User Data Encryption
User data encryption is enabled by default on the customer platform. All reads and writes to the /home directory are encrypted. On boot, during file system setup, the startup scripts mount the user data in the encrypted /home directory.
To change the size of the user data disk
1. Modify the size parameter for the EFS_USR_DAT_ECRYPT_PART partition.
The default size is 5 GB.
2. After boot, dump the disk partitions by executing the command:
$df -h
The new encrypted partition is displayed with the name EFS_USR_DAT_ECRYPT_PART.
3. To obtain more information about the encrypted partition, execute the command:
$cryptsetup status /dev/mapper/dev-32e7bcd8-0561-4946-9c3e-8a0f314357a2
4. Execute this command also provides information about the encrypted partition.
$dmsetup status
A systemd service mounts the encrypted disk at the /home directory on every boot. All accesses to the disk is then encrypted. This occurs transparently without user interference.
Data Encryption Impact on Boot Times
On the first boot, after flashing, setting up the encrypted partition takes about 15 minutes. The setup involves:
• Initializing the encrypted partition with random data
• Mounting the encrypted partition on /home directory
After the first boot, subsequent reboots do NOT have an impact on boot times.
Encryption Algorithm
The cipher mode used for disk encryption is aes-cbc-essiv:sha256. The cipher generator consists of three parts: cipher-chainmode-IV generator.
Consult the Linux documentation for more information at:
Disk Encryption Key Management
Two types of keys are provided for Encrypted File System (EFS) functionality:
• Disk Encryption Key (DEK) is also known as the master key. The disk encryption key is ensures the data flowing between the file system and the disk is encrypted and decrypted.
• Passphrase/Password is the string or pattern input provided by the user to setup disk encryption. The same input is later used to enter, unlock, and decrypt the user data data. In an automotive usecase, it is assumed that there is no user interaction to setup or enter a passphrase each time. Consequently, the system sets and stores a passphrase that is used on every boot.
Hardware Backed Disk Encryption Key
The Disk Encryption Key (DEK) is derived from a /dev/urandom buffer with 32 bytes of random data. To enhance security and add randomness, the random buffer is then HMAC-SHA-256 signed in the secure world and returned back to cryptsetup. The secret key portion for the Hash Message Authentication Code (HMAC) tag is derived from the EKS blob provisioned into the device as follows:
To derive the hardware backed passphrase
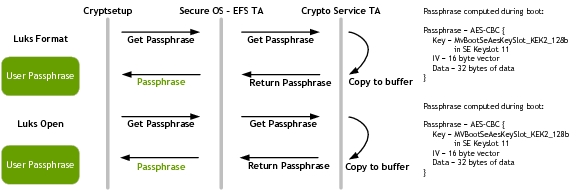
Obtaining the Initial Passphrase
The initial passphrase is derived by performing an AES-CBC-128 encryption of a fixed known buffer, known as IV. The key is stored in the KEK2 hardware fuse provisioned by the OEM.
It is assumed that the OEM has some MAC layer, such as SE Linux, to verify that the clients calling into the trusted operating system are validated or access controlled. This is required to ensure that a passphrase is not given out to unknown clients.
The flow for obtaining the initial passphrase is as follows:
A keyfile is also created during the first boot with a 32 byte random vector from /dev/urandom, accessible by the kernel.
If the trust zone call to get a passphrase is not supported on your platform, the passphrase in the keyfile is used as a secondary/backup option for the initial passphrase. The keyfile is stored in the usr partition of the root-file system.
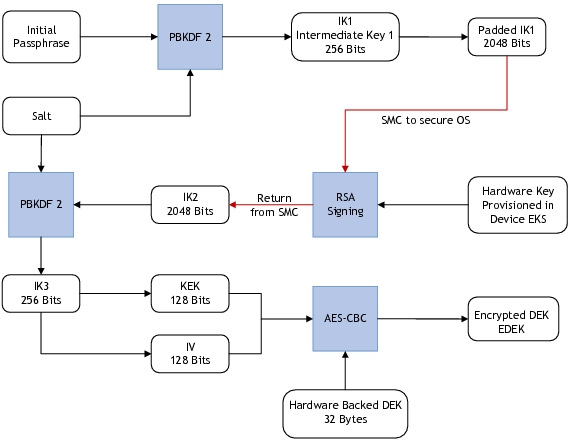
Deriving the Hardware Backed Passphrase
To derive the hardware backed passphrase, the initial passphrase is run through the state machine as follows:
The cryptsetup encrypts the hardware backed DEK using the hardware backed passphrase and stores the encrypted DEK on the encrypted partition.
Building Cryptsetup with Hardware Backed Changes
The platform contains native cryptsetup code and the changes made by NVIDIA to support hardware backed passphrase and DEK.
The sources, headers, and build scripts are available at:
drive-<platform>-linux/samples/security/cryptsetup
To build cryptsetup
• Execute the command:
$./build_cryptsetup_pdk.sh
If the build was successful, a message similar to the following is displayed:
Cryptsetup build complete. Check src/.libs/ for the executables
To rebuild cryptsetup
• Execute these commands, for incremental builds:
$cd cryptsetup-1.6.3
$make
• Execute these commands, for clean builds:
$cd cryptsetup-1.6.3
$make clean
$make