Vulnerability Response#
Once software has been published, it must be maintained, and this includes addressing any vulnerabilities that may be discovered after publication. In this section, we will go over how NVIDIA helps customers maintain the security of our software after deployment.
Vulnerability Scanning#
NVIDIA uses industry-standard vulnerability scanning methods for container images. All identified packages are scanned against security feeds to detect known vulnerabilities accurately. To reduce the noise inherent in such scanning efforts, the following logic of applying the severity score is used:
For non-operating system packages (e.g. Python), GitHub Advisory (GHSA) matching and severity determination is applied to a given known vulnerability in a package.
For operating system packages (e.g. Debian), the severity score, as determined by the specific distro security feed on which the container image is based, is applied, such as Ubuntu Security Notices.
For any remaining packages in the image that have no matching from 1 and 2 above, the NIST National Vulnerability Database (NVD) is applied with its severity scoring.
Vulnerability scanning at NVIDIA occurs during three distinct phases in the product lifecycle: iteratively during development, during the publishing process to the NGC Catalog (no Critical or High vulnerabilities allowed for publishing), and then as part of continuous scanning of published containers on the NGC Catalog. As new vulnerabilities are reported, these issues are tracked and included in the NVIDIA security risk score.
Software designated as Government ready follows additional scanning policies to meet the baseline requirements for FedRAMP High or equivalent environments.
Vulnerability Patching#
At NVIDIA, we prioritize patching vulnerabilities categorized as critical and high severity based on the Common Vulnerability Scoring System (CVSS) and our scanning logic before any release. Our patching strategy adapts to the specific branch type offering roll-forward fixes for feature branches and scheduled updates (monthly for production branches or quarterly for long-term supported branches) while ensuring API stability. For specific OSS packages, NVIDIA partners with Canonical to provide vulnerability patching support for enterprise containers.
Software designated as Government ready follows an SLA based patching policy to meet the baseline requirements for FedRAMP High or equivalent environments.
Vulnerability Exploitability eXchange (VEX)#
In circumstances when a vulnerability cannot be addressed, such as when it has been recently discovered, or there is no available fix, an exception process with documentation is used.
NVIDIA extends its commitment to security by providing detailed advisories and exploitability information in Vulnerability Exploitability Exchange (VEX) documents. Unlike CVE entries, VEX documents offer context-specific insights into vulnerabilities, identifying their relevance and exploitability within particular components of the AI stack. Facilitated by the CycloneDX format, this enables effective, machine-readable communication, enhancing our customers’ security posture.
NVIDIA issues VEX documents in the following cases:
NVIDIA or Canonical has patched an open-source software component. However, a customer’s container scanner may still identify this component as vulnerable, which is noted in the VEX document.
The detected vulnerability cannot be exploited because mitigating circumstances are in place.
The detected vulnerability is a false positive.
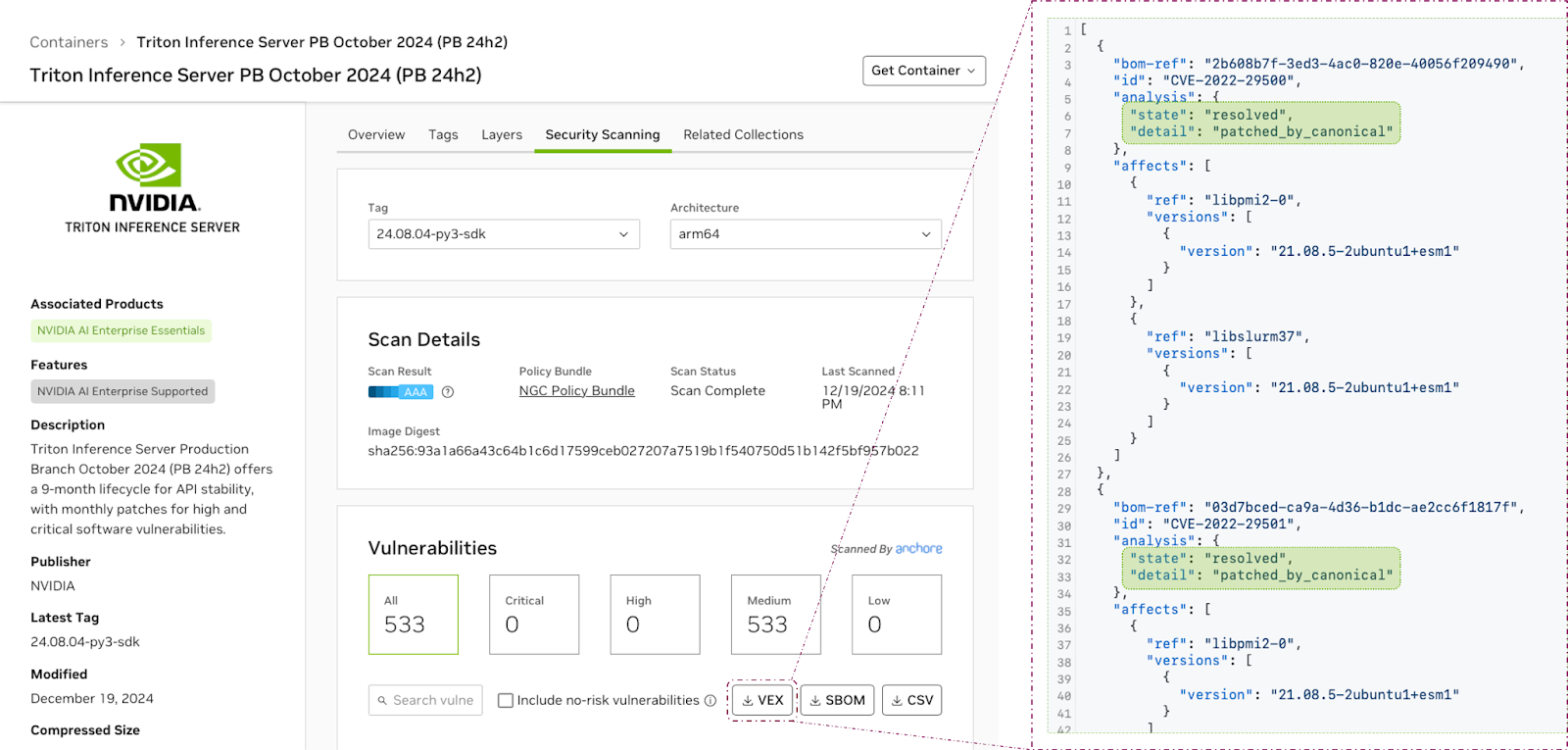
Figure 4 VEX for Enterprise Containers on NGC Catalog#
Coordinated Vulnerability Disclosure#
The NVIDIA Product Security Incident Response Team (PSIRT) manages the receipt, investigation, internal coordination, remediation, and disclosure of potential security vulnerabilities related to NVIDIA products. The team aims to minimize customers’ risk associated with security vulnerabilities by providing timely notification, guidance, and remediation of vulnerabilities in our products and services.
We publish a detailed security bulletin on our public website whenever a security issue is identified.
We also participate in Coordinated Vulnerability Disclosure. PSIRT follows ISO/IEC 29147/30111. The standard is developed and maintained by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC).
Security Incident Monitoring#
Customers can report security issues at any time to NVIDIA Enterprise Support, and the information will be forwarded to the PSIRT team for analysis.
NGC Notification Service#
The NGC Notification Services feature enables NVIDIA AI Enterprise users to subscribe to email notifications to receive service change events. By subscribing to notifications, users can stay updated with the latest changes and developments in the NGC cloud platform and its services. NGC customers can be informed of the following types of changes:
Customer-impacting service enhancements (release notes)
Security vulnerabilities (CVEs) and scanning reports
Software end-of-life announcements
Scheduled web portal maintenance to an NGC property
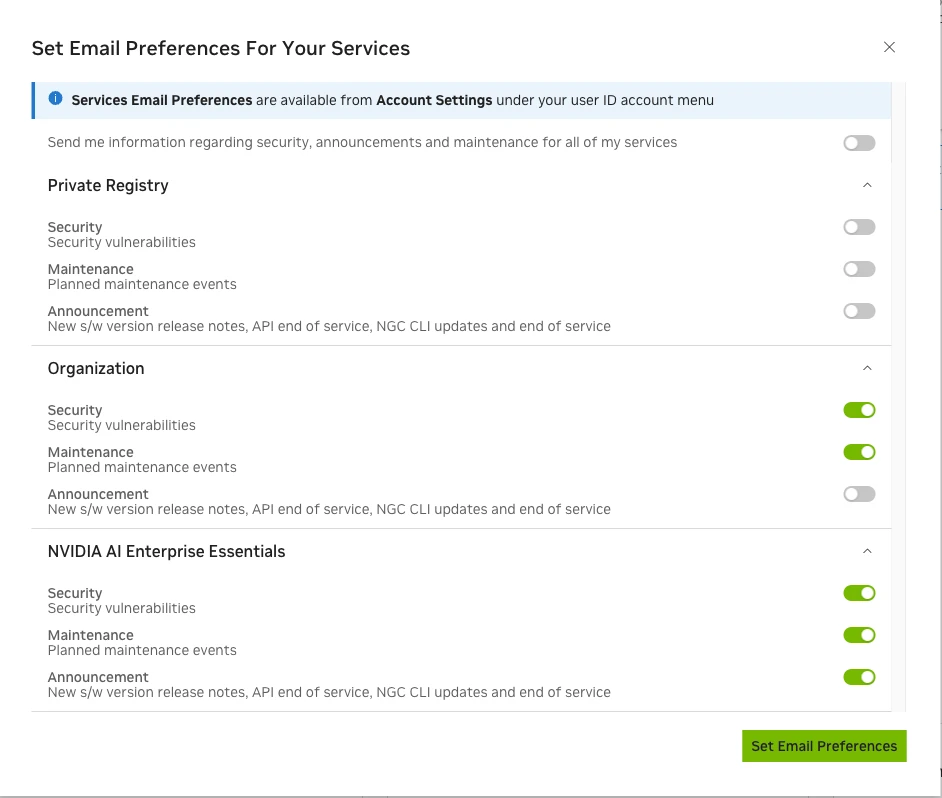
Figure 5 Notification Services available for Enterprise Users on NGC Catalog#