Setup Guide#
This document provides a comprehensive guide for deploying Tokkio Workflow on Microsoft Azure. While multiple approaches exist for implementing Tokkio Workflow in the Azure Cloud environment, this guide focuses on a specific deployment method utilizing Tokkio’s opinionated deployment scripts. These scripts automate the process of setting up Tokkio Workflow along with its required infrastructure components.
Prerequisites#
Azure setup#
Azure account with admin access
Azure service principal to enable the automated deployment scripts to authenticate themselves with
Azure storage account and container to host the state of the automated deployment scripts, so that the created infrastructure may be modified or torn down at a later date or time
Registered domain for hosting Tokkio Application
Azure app certificate for SSL support
For instructions on how to set this up, refer to the Azure documentation. You may also follow the instructions in Environment Variables And Prerequisites Setup section.
Hardware#
Controller instance#
Ubuntu 22.04 Operating system
Generate an SSH key pair
Ensure passwordless sudo access
Access#
Access to all the artifacts used during the bringing up of Tokkio Pipeline Application. For e.g. Tokkio Application Helm chart on NGC.
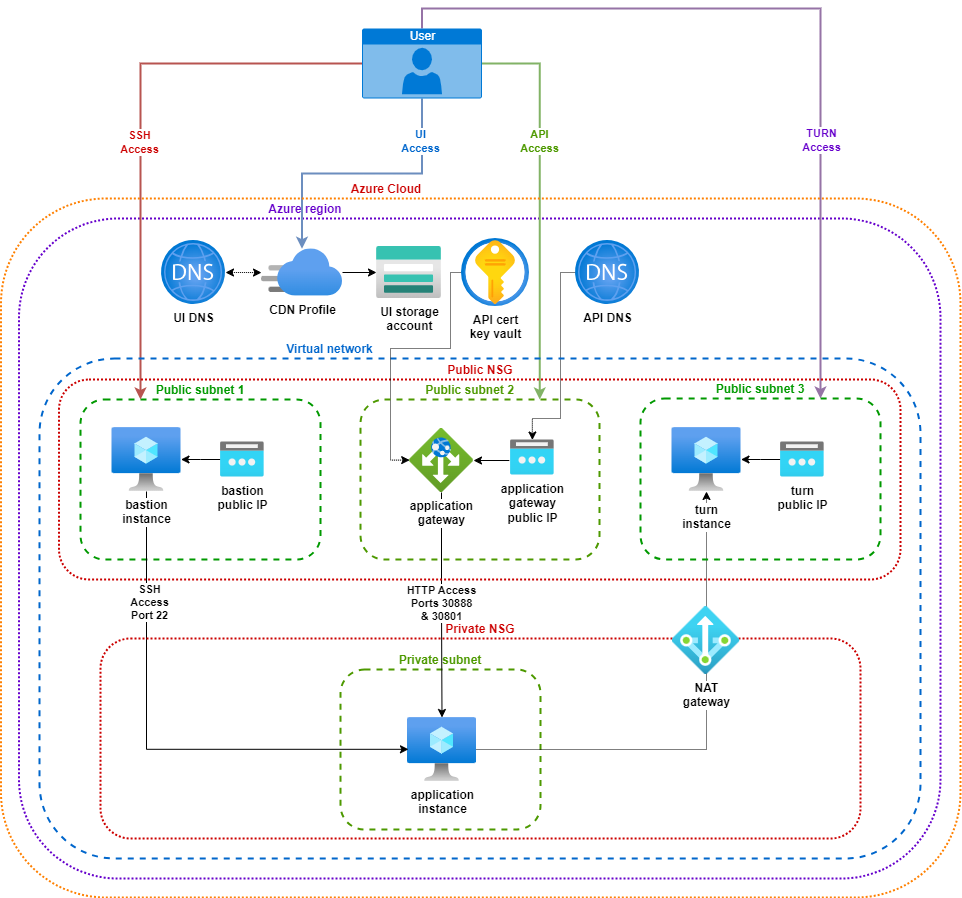
Infrastructure Layout#
Tokkio Workflow setup on Azure requires several Azure resources to be created such as Virtual Machines, Network Security Groups, Application Gateways, FrontDoor CDN for hosting UI content, etc., Below diagram shows the infrastructure layout this Deployment script is going to create.
Installation Steps#
Clone the NVIDIA/ACE.git repository and navigate to the azure deployment scripts directory
git clone https://github.com/NVIDIA/ACE.git
cd ACE/workflows/tokkio/4.1/scripts/one-click/azure
Prepare a config file, either by copying base
config-template.ymlor by copying one of the example config files available underconfig-template-examplesfolder.
#list of example templates
config-template-examples/
├── llm-ov-3d-rp-3x-streams
│ ├── config-template.yml
│ └── my-config.env
└── llm-ue-3d-coturn-3x-streams
├── config-template.yml
├── my-config.env
└── user-helm-override-values.yml
Copy a config template of your choice as base config template for this installation.
cp config-template-examples/llm-ov-3d-rp-3x-streams/config-template.yml ./my-config.yml
Modify the
my-config.ymlwith your specific settings
vi my-config.yml
Set up environment variables.
Similar to
config-templatefile, you can copy an example env file fromconfig-template-examplesfolderModify environment variables file with your specific settings
cp config-template-examples/llm-ov-3d-rp-3x-streams/my-config.env my-env-file.env
vi my-env-file.env
Source the environment variables file
source my-env-file.env
Run the installation command
./envbuild.sh install --component all --config-file ./my-config.yml
Capture installation results at the end of logs. Output will look like the sample below.
access_urls:
api_endpoint: "https://<api_sub_domain>.<base_domain>"
elasticsearch_endpoint: "https://elastic-<name>.<base_domain>"
grafana_endpoint: "https://grafana-<name>..<base_domain>"
kibana_endpoint: "https://kibana-<name>..<base_domain>"
ui_endpoint: "https://<ui_sub_domain>.<base_domain>"
ssh_command:
app:
bastion: ssh -i /home/my-user/.ssh/id_rsa -o StrictHostKeyChecking=no -o UserKnownHostsFile=/dev/null <username>@<bastion-instance-ip-address>
master: ssh -i /home/my-user/.ssh/id_rsa -o StrictHostKeyChecking=no -o UserKnownHostsFile=/dev/null -o ProxyCommand="ssh -i /home/my-user/.ssh/id_rsa -o StrictHostKeyChecking=no -o UserKnownHostsFile=/dev/null -W %h:%p <username>@<bastion-instance-ip-address>" <username>@<app-instance-ip-address>
turn:
master: ssh -i /home/my-user/.ssh/id_rsa -o StrictHostKeyChecking=no -o UserKnownHostsFile=/dev/null <username>@<turn-instance-ip-address>
Verify installation
Check pod status:
kubectl get pods \-n \<application-namespace\>Wait for all pods to reach Ready status (may take up to 60 minutes)
Once all the pods are healthy you can access the UI using the URL from installation output
access_urls.ui_endpointFor the first time, the browser should prompt permissions such as Mic, Speaker or Camera necessary for the UI to operate. Upon accepting the permissions, the UI should load.
Uninstallation Steps#
Uninstalling Just The Application#
Source the correct environment variables file
source my-env-file.env
Run the below commands to uninstall just the application components
./envbuild.sh uninstall --component app --config-file ./my-config.yml
Clear any
persistent-volumesfrom previous installation by below command
kubectl delete pv -n <application-namespace>
Uninstalling The Whole Setup#
Source the correct environment variables file
source my-env-file.env
Run the below un-install command
./envbuild.sh uninstall --component all --config-file ./my-config.yml
Caution
This step uninstalls the entire Kubernetes cluster, Azure infrastructure that was brought up during the install step. So use this with caution.
Additional Considerations#
Cost#
Many of the resources in this setup may not fall within Azure’s Free tier. To understand the cost implications, you should consult the Azure pricing calculator and Azure Cost Management, Billing documentation.
Security#
The security of Tokkio in production environments is the responsibility of the end users deploying it. When deploying in a production environment, please have security experts review any potential risks and threats; define the trust boundaries, secure the communication channels, integrate AuthN & AuthZ with appropriate access controls, keep the deployment including the containers up to date, ensure the containers are secure and free of vulnerabilities.
Essential Skills And Background#
Familiarity With Azure CSP#
Users should have a basic understanding of the Azure Cloud Solution Provider program, including its billing model and available services.
Familiarity with Azure Resource Manager (ARM) is crucial, as all services in CSP are based on the ARM deployment model
Users should be aware of any CSP-specific limitations or restrictions that may affect the deployment of certain Azure services or offers
Additionally, knowledge of CSP-specific tools and portals for managing customer subscriptions, provisioning services, and handling support is beneficial and will help in effectively deploying and managing Tokkio on Azure CSP
Familiarity With Command-Line-Interface (CLI)#
Basic Commands: Users should be comfortable with basic command-line operations, such as navigating directories, executing scripts, and managing files.
Environment Configuration: Understanding how the environment variables and how PATH setup works on Linux will greatly help operating OneClick script.
Scripting Basics: Basic scripting knowledge (e.g., shell scripting) is beneficial for understanding how the OneClick script operates and for troubleshooting any issues that may arise.
Familiarity With YAML#
YAML Syntax and Structure: YAML is often used for configuration files in cloud-native applications due to its readability and flexibility. The Configuration templates used in OneClick script uses YAML format. Users should be familiar with YAML syntax and structure.
Familiarity With Kubernetes Eco System#
Tokkio pipeline is a Cloud native application, and uses concepts like Containerization, Kubernetes, helm etc. Users need to be familiar with these to get the best results from using the deployment scripts and the app.
Kubernetes Basics: Users should have basic understanding of Kubernetes core concepts such as pods, services and deployments
kubectl: Familiarity with the kubectl the command line tool used to interact with Kubernetes clusters including querying the status or logs of Running application pods etc.
Helm: Understanding Helm package manager for Kubernetes that simplifies application deployment by managing charts (collections of pre-configured Kubernetes resource definitions). And how to use helm with override values will help configuring the templates appropriately.