Connecting to BMC Interfaces
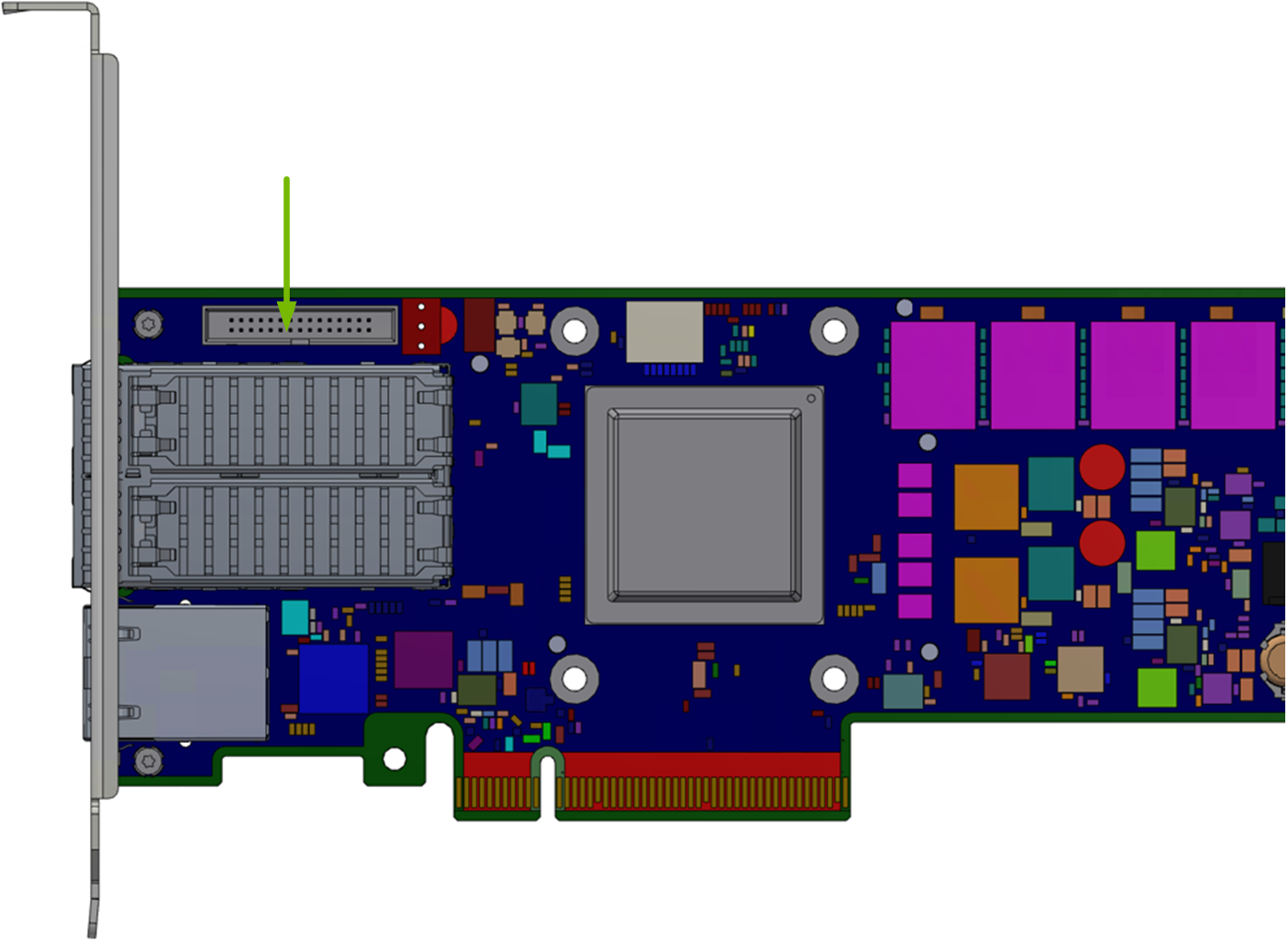
The BMC UART1 console is available on the IO panel. The BMC is connected to a 30-pin flat cable connector which allows the Linux console to be monitored.
NVIDIA® BlueField®-3 BMC Connector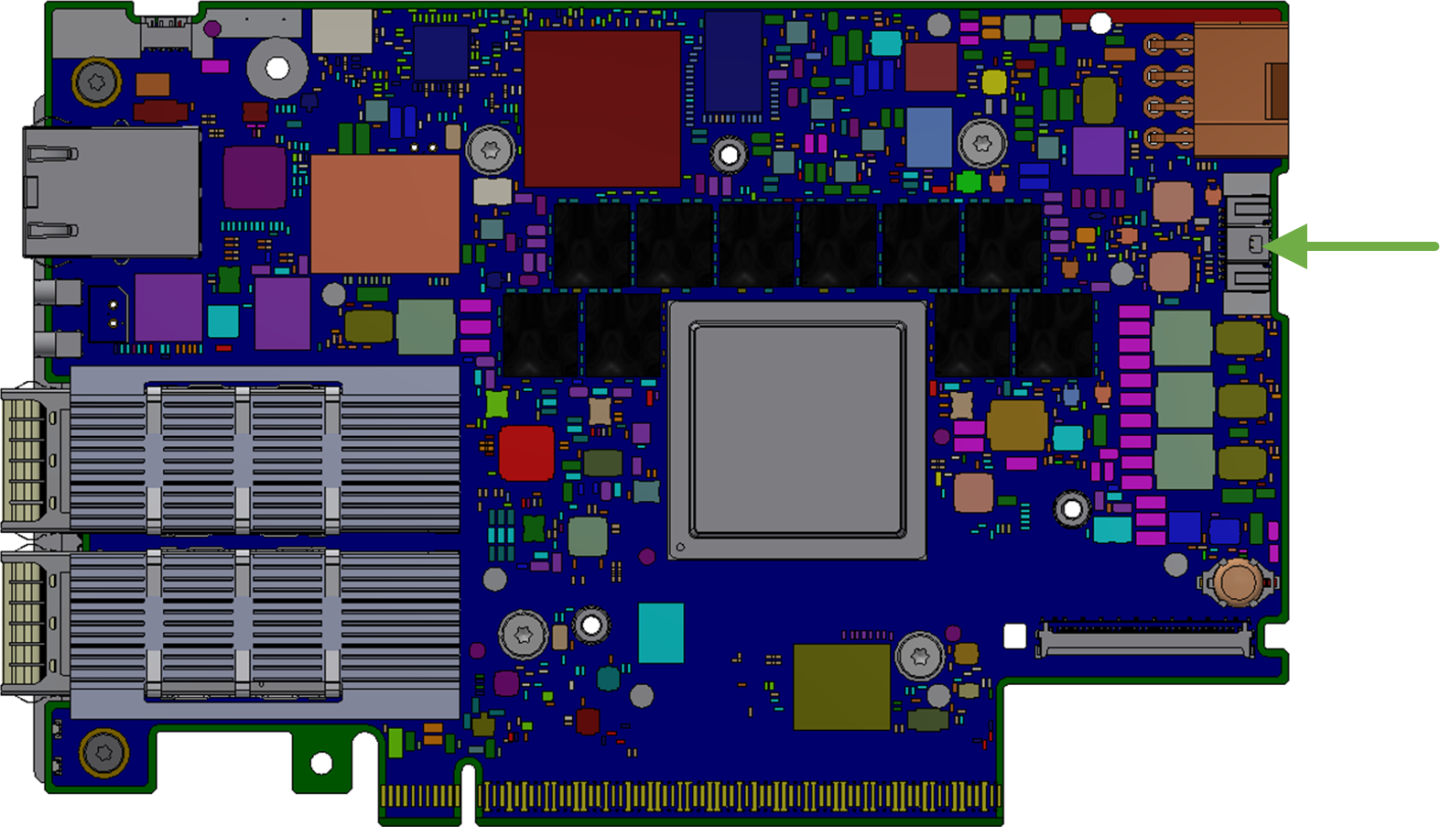
NVIDIA® BlueField®-2 BMC Connector
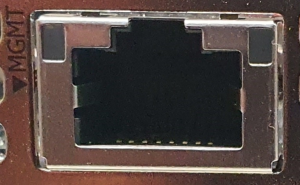
The BMC has a separate Ethernet interface which provides network connection for management traffic to the BMC. The DPU's bracket has an RJ45 port labeled "MGMT" which is the management interface port. The management port is configured with auto-negotiation capabilities by default (100MbE to 1GbE).
The BMC interface eth0 is the management interface, so any information displayed by "ifconfig eth0" pertains to the management interface. The MAC address to be used for eth0 is pre-programmed in the BMC FRU EEPROM and can be found on the DPU's board label. By default, the IP address used for eth0 is acquired via DHCP but can be configured differently.
Changing Default Password
When initially logging into the system, it is mandatory to update the default BMC password, 0penBmc. The DPU BMC offers two methods/interfaces for changing the password:
SSH/serial:
To change the password, connect to the BMC via SSH/serial and log in using the root user and the default password. Upon logging in, you are prompted with the following:
dpu-bmc login: root Password: <Type the default Password> You are obliged to immediately change your password (mandatory
foradministrators). Changing the root password. Current password: <Re-Type the default Password> New password: <Type the new Password according to the above rules> Retype the new password: <Re-Type the new Password>Redfish:
The Redfish user management interface may be used to configure the new password. The following Redfish command can be employed to alter the default password:
curl -k -u root:0penBmc -H
"Content-Type: application/json"-X PATCH https://<IP>/redfish/v1/AccountService/Accounts/root -d'{"Password" : "<PASSWORD>"}'
The new password must comply with the following policy parameters:
Minimum length: 13
Maximum length: 20
Minimum number of upper-case characters: 1
Minimum number of lower-case characters: 1
Minimum number of digits: 1
Minimum number of special characters: 1
NoteList of special characters:
$ (dollar sign)
% (percent sign)
^ (caret/circumflex)
& (ampersand)
* (asterisk)
- (minus)
+ (plus)
= (equal)
| (pipe)
~ (tilde)
_ (underscore)
, (comma)
. (period/full stop)
; (semicolon)
: (colon)
" (quotation mark)
' (apostrophe)
/ (forward slash)
\ (backslash)
Maximum number of consecutive character pairs: 4
NoteTwo characters are consecutive if |hex(char_1)-hex(char_2)|=1.
Examples of passwords with 5 consecutive character pairs (invalid): DcBa123456AbCd!; ab1XbcYcdZdeGef!; Testing_123abcgh!.
The root account locks after four consecutive failed attempts and automatically unlocks after 10 minutes.
Account Service
The Redfish root user can inquire about and modify the applied account policies, which encompass settings such as the number of consecutive login attempts permitted and the time period for which the system will remain locked.
The following Redfish command provides the current settings:
curl -k -u root:'ubuntu&3Tango11' -H 'Content-Type: application/json' -X GET https://10.237.53.58/redfish/v1/AccountService
{
"@odata.id": "/redfish/v1/AccountService",
"@odata.type": "#AccountService.v1_10_0.AccountService",
"AccountLockoutDuration": 600,
"AccountLockoutThreshold": 4,
"Accounts": {
"@odata.id": "/redfish/v1/AccountService/Accounts"
},
"ActiveDirectory": {
"Authentication": {
"AuthenticationType": "UsernameAndPassword",
"Password": null,
"Username": ""
},
"LDAPService": {
"SearchSettings": {
"BaseDistinguishedNames": [
""
],
"GroupsAttribute": "",
"UsernameAttribute": ""
}
},
"RemoteRoleMapping": [],
"ServiceAddresses": [
""
],
"ServiceEnabled": false
},
"Description": "Account Service",
"Id": "AccountService",
"LDAP": {
"Authentication": {
"AuthenticationType": "UsernameAndPassword",
"Password": null,
"Username": ""
},
"Certificates": {
"@odata.id": "/redfish/v1/AccountService/LDAP/Certificates"
},
"LDAPService": {
"SearchSettings": {
"BaseDistinguishedNames": [
""
],
"GroupsAttribute": "",
"UsernameAttribute": ""
}
},
"RemoteRoleMapping": [],
"ServiceAddresses": [
""
],
"ServiceEnabled": false
},
"MaxPasswordLength": 20,
"MinPasswordLength": 13,
"Name": "Account Service",
"Oem": {
"OpenBMC": {
"@odata.id": "/redfish/v1/AccountService#/Oem/OpenBMC",
"@odata.type": "#OemAccountService.v1_0_0.AccountService",
"AuthMethods": {
"BasicAuth": true,
"Cookie": true,
"SessionToken": true,
"TLS": true,
"XToken": true
}
}
},
"Roles": {
"@odata.id": "/redfish/v1/AccountService/Roles"
},
"ServiceEnabled": true
}
By default, if a user attempts to log into the system with an incorrect password four times in a row, their account is locked for 600 seconds. Afterwards, the user is allowed another opportunity to log in with the correct credentials. If the user fails to log in again, the account is immediately locked for an additional 600 seconds. If the user logs in successfully, the counter of consecutive login failures is reset.
The patch command may be used to modify the default policy settings. The following example illustrates how to alter the number of allowed consecutive login attempts into the system.
curl -k -u root:'<PASSSWORD>' -H 'Content-Type: application/json' -X PATCH https://<IP>/redfish/v1/AccountService -d '{"AccountLockoutThreshold" : 10}'
For a comprehensive understanding of the schema, please refer to the DMTF definition of the AccountService.v1_10_0.AccountService schema.
If an account becomes inaccessible, users may check the system's status using the Redfish interface using the following GET operation:
curl -k -u root:'<PASSWORD>' -H 'Content-Type: application/json' -X GET https://<IP>/redfish/v1/AccountService
{
"error": {
"@Message.ExtendedInfo": [
{
"@odata.type": "#Message.v1_1_1.Message",
"Message": "While accessing the resource at '/redfish/v1/AccountService', the service received an authorization error 'Account temporarily locked out for 600 seconds due to multiple authentication failures'.",
"MessageArgs": [
"/redfish/v1/AccountService",
"Account temporarily locked out for 600 seconds due to multiple authentication failures"
],
"MessageId": "Base.1.15.0.ResourceAtUriUnauthorized",
"MessageSeverity": "Critical",
"Resolution": "Ensure that the appropriate access is provided for the service in order for it to access the URI."
}
],
"code": "Base.1.15.0.ResourceAtUriUnauthorized",
"message": "While accessing the resource at '/redfish/v1/AccountService', the service received an authorization error 'Account temporarily locked out for 600 seconds due to multiple authentication failures'."
}
}
Do not manually modify the network configuration file /etc/systemd/network/00-bmc-eth0.network.
There are two ways of configuring the network interfaces:
Dynamic (DHCP)
Static
Dynamic Address Configuration
T o facilitate the DHCP server's recognition of the DPU BMC as the address requester, the BMC is configured to incorporate the DHCPv4/6 vendor class ID (option 60) set to NVIDIA/BF/BMC .
Run the following:
busctl set-property xyz.openbmc_project.Network /xyz/openbmc_project/network/eth0 xyz.openbmc_project.Network.EthernetInterface DHCPEnabled b 1
Static
Set static address on the interface. Run:
busctl call xyz.openbmc_project.Network /xyz/openbmc_project/network/<interface> xyz.openbmc_project.Network.IP.Create IP ssys
"xyz.openbmc_project.Network.IP.Protocol.IPv4""<IP Address>"<Netmask Prefix>"<Network Gateway>"Configure default gateway. Run:
busctl
set-property xyz.openbmc_project.Network /xyz/openbmc_project/network/config xyz.openbmc_project.Network.SystemConfiguration DefaultGateway s"<DefaultGateway>"
This section describes the use cases for the BMC USB port. Note that only BMC Linux has access to the USB port and its feature set. There is no access to BMC USB port while running u-boot.
Due to a hardware bug in AST2500, the USB interface is only able to work at USB 1.0 speeds.
Storage device support on this port has only been validated with USB flash drives.
Providing Removable Storage via USB Stick
Once a USB stick is plugged in to the BMC's USB port, issue the command lsusb and/or check the dmesg log to see if the USB stick has been detected. The successful insertion of a USB stick will create a device under /dev called sda (or sdb), and a mountable partition /dev/sda1. To mount the USB stick as a filesystem, just issue the command "mount /dev/sda1 /mnt" to mount it at /mnt. The command "umount /mnt" unmounts the device.