Mutual TLS (mTLS) Configuration
Mutual TLS ( mTLS) , is a security protocol that ensures both the client and server in a network communication authenticate each other using certificates before establishing a connection. This is an enhancement over standard Transport Layer Security (TLS), where only the server is authenticated by the client.
In this release, mTLS is enabled by default in NMX-M. NMX-M communicates with both NMX-T and NMX-C using mTLS over gRPC, therefore, please make sure that mTLS is also configured on both NMX-T and NMX-C.
The procedures below must be performed after the NMX-M deployment.
Make sure to generate and provide the location of the certificates when scripts prompt for it before running the following script.
Ensure that the certificates used by NMX-M, NMX-T, and NMX-C are either issued by the same CA or signed by a CA that is trusted and approved.
From the Ansible folder run the following command.
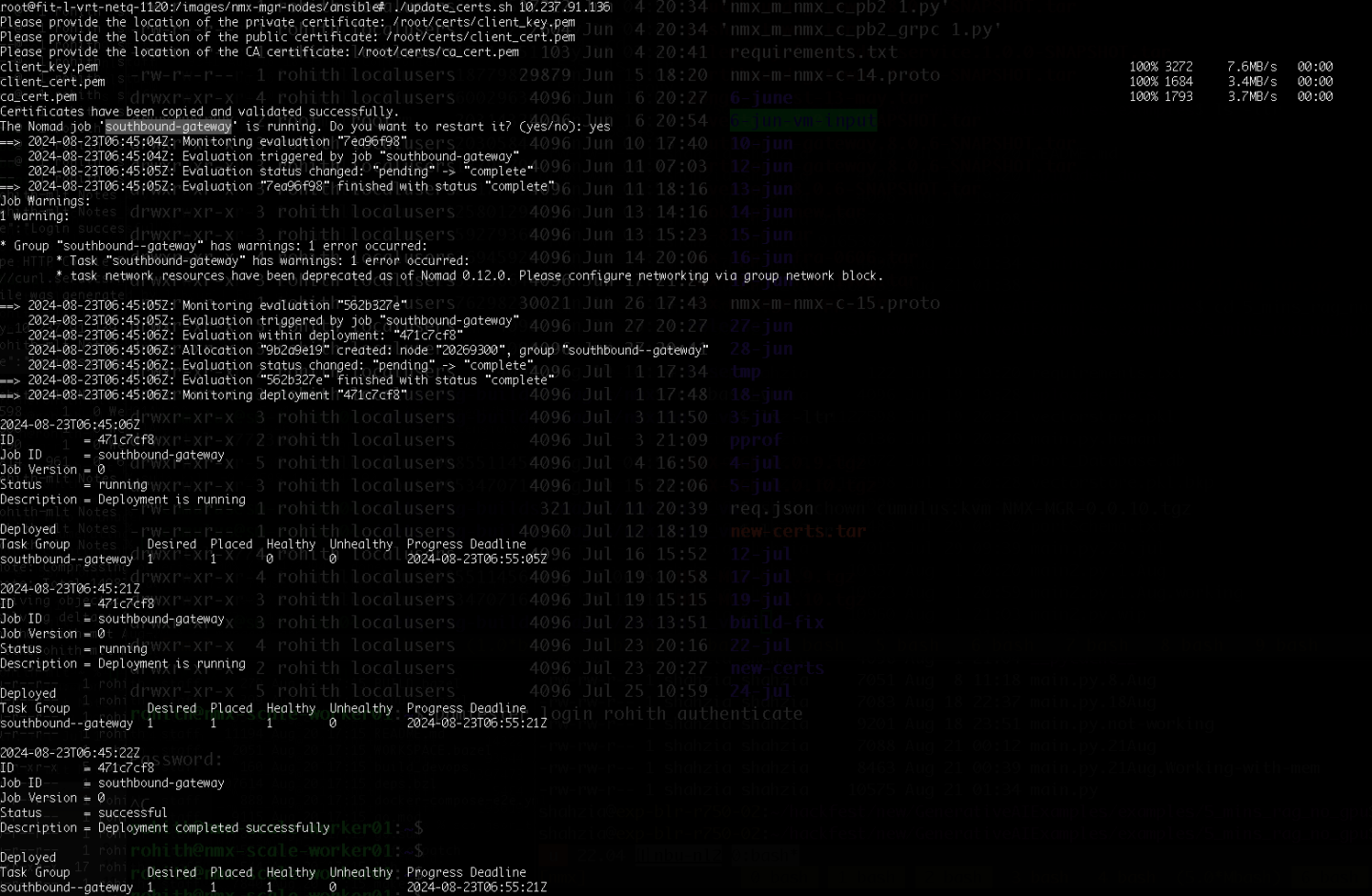
#update_certs.sh <ip of the VM>
Select 'yes' when prompted to reboot the southbound-gateway.
The below is an output sample. Please ensure to provide the certificate path specific to your environment.
This step is required only if authentication is failing due to a SAN header check.
To bypass the SAN header check, use the following script to update the mTLS configuration and skip SAN validation.
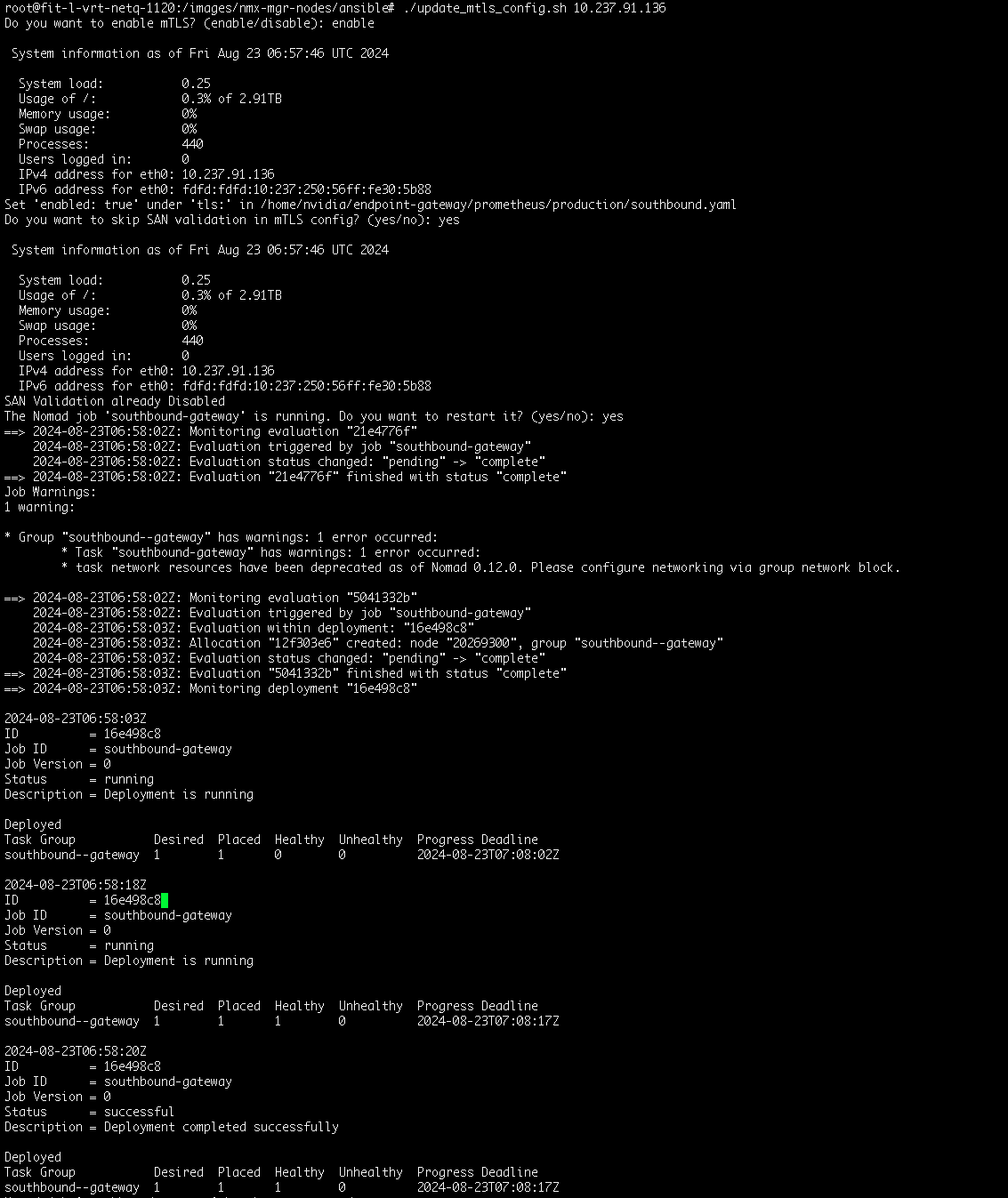
#update_mtls_config.sh <ip of the VM>
Select 'enable' when prompted to enable mTLS.
Select 'yes' when prompted to skip SAN validation in mTLS configuration.
Select 'yes' when prompted to reboot the southbound-gateway.
The below is an output sample.