Token-based Authentication
Token-based authentication is a protocol which allows users to verify their identity, and in return receive a unique access token. During the life of the token, users then access the UFM APIs that the token has been issued for, rather than having to re-enter credentials each time they need to use any UFM API.
Under the Settings section there is a tab titled called “Access Tokens”.
The functionality of the added tab is to give the user the ability to create new tokens & manage the existing ones (list, copy, revoke, delete):
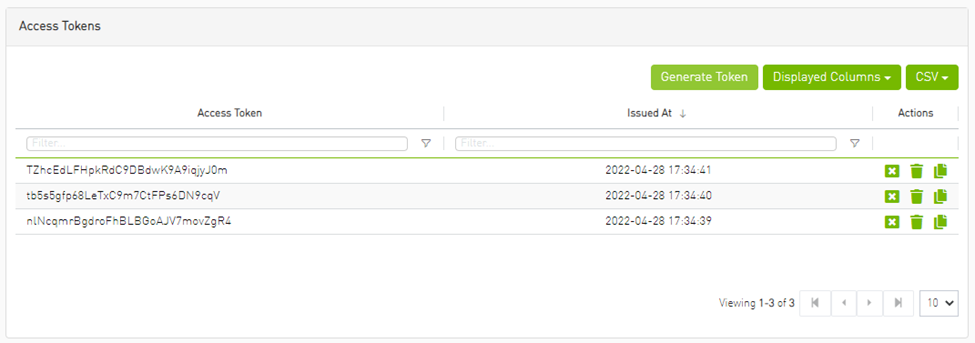
Actions:
|
Name |
Icon |
Description |
|
Revoke |
|
Revoke a specific token. Note
The revoked token will no longer be valid.
|
|
Delete |
|
Delete a specific token. |
|
Copy |
|
Copy specific token into the clipboard. |
Each user is able to list and manage only the tokens that have been created by themselves. Only the users with system_admin role will be able to create tokens.


