UEFI Secure Boot
This feature is available in NVIDIA® BlueField®-2 DPUs and up.
UEFI secure boot is a feature of the Unified Extensible Firmware Interface (UEFI) specification. The feature defines a new interface between the OS and firmware/BIOS.
When enabled and fully configured on the DPU, UEFI secure boot helps the Arm-based software running on top of UEFI resist attacks and infection from malware. UEFI secure boot detects tampering with boot loaders, key operating system files, and unauthorized option ROMs by validating their digital signatures. Detections are blocked from running before they can attack or infect the system.
UEFI secure boot works like a security gate. Code signed with valid keys (whose public key/certificates exist in the DPU) gets through the gate and executes. However, UEFI secure boot blocks at the gate and rejects a code that has a bad signature or no signature.
The DPU enables UEFI secure boot with the Ubuntu OS that is included in the platform software.
Verifying UEFI Secure Boot on DPU
To verify whether UEFI secure boot is enabled, run the following command from the BlueField console:
ubuntu@localhost:~$ sudo mokutil --sb-state
SecureBoot enabled
As UEFI secure boot is not specific to BlueField platforms, refer to the Canonical documentation online for further information on UEFI secure boot to familiarize yourself with the UEFI secure boot concept:
Main Use Cases for UEFI Secure Boot
UEFI secure boot can be used in 2 main cases for the DPU:
|
# |
Method |
Pros |
Cons |
|
1 |
Using the default enabled UEFI secure boot (with Ubuntu OS or any Microsoft signed boot loader) Warning
See section "Using Default Enabled UEFI Secure Boot" for more
|
Relatively easy |
Limited flexibility; only allows executing NVIDIA binary files |
|
Dependency on Microsoft as signing entity |
|||
|
2 |
Enabling UEFI secure boot with a user/custom OS (other than the default Ubuntu) Warning
Please contact NVIDIA Networking Support for instructions
|
Autonomy – you control your keys (no dependency on Microsoft or NVIDIA as signing entities) |
Necessitates creating your own capsule files to enroll and customize UEFI secure boot |
Signing binaries is complex as you must create X.509 certificates and enroll them in UEFI or shim which requires a fair amount of prior knowledge of how secure boot works. For that reason, BlueField secured platforms are shipped with all the needed certificates and signed binaries (allowing seamless work with case #1).
NVIDIA strongly recommends utilizing UEFI secure boot in any case due the increased security it enables.
UEFI secure boot is enabled as part of the default settings of the DPU and requires no special configuration from the user to use with the bundled Ubuntu operating system.
Disabling UEFI Secure Boot
UEFI secure boot can be disabled per device from the UEFI menu as part of the DPU boot process, which requires access to the BlueField console.
To disable UEFI secure boot, reboot the platform and stop at the UEFI menu. From the UEFI menu screen, select "Device Manager", then "Secure Boot Configuration". If "Attempt Secure Boot" is checked, then uncheck it and reboot.
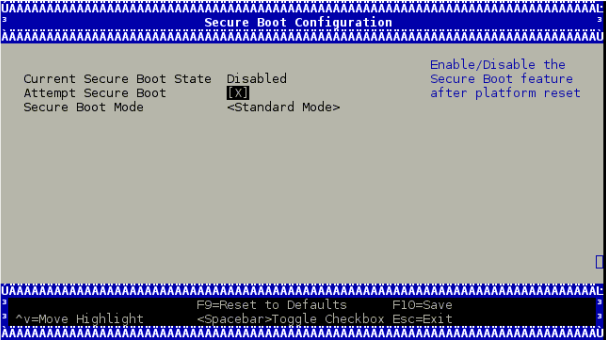
Disabling secure boot permanently is not recommended in production environments.
Existing DPU Certificates
As part of having UEFI secure boot enabled, the UEFI databases are populated with NVIDIA self-signed X.509 certificates. The Microsoft certificate is also installed into the UEFI database to ensure that the Ubuntu distribution can boot while UEFI secure boot is enabled (and generally any DPU-compatible OS loader signed by Microsoft).
The pre-installed certificate files are:
NVIDIA PK key certificate
NVIDIA KEK key certificate
NVIDIA db certificate
Microsoft db certificate