Modes of Operation
The NVIDIA® BlueField® DPU has several modes of operation:
Embedded function (ECPF) ownership where the embedded Arm system controls the NIC resources and data path (default)
Restricted mode which is an extension of the ECPF ownership with additional restrictions on the host side
Separated host mode (symmetric model)
This mode, known also as ECPF or DPU mode, is the default mode for BlueField DPU.
In ECPF mode, the NIC resources and functionality are owned and controlled by the embedded Arm subsystem. All network communication to the host flows through a virtual switch control plane hosted on the Arm cores, and only then proceeds to the x86 host. While working in this mode, the DPU is the trusted function managed by the data center and host administrator—to load network drivers, reset an interface, bring an interface up and down, update the firmware, and change the mode of operation on the DPU device.
A network function is still exposed to the host, but it has limited privileges. In particular:
The driver on the host side can only be loaded after the driver on the DPU has loaded and completed NIC configuration.
All ICM (Interface Configuration Memory) is allocated by the ECPF and resides in the DPU's memory.
The ECPF controls and configures the NIC embedded switch which means that traffic to and from the host (DPU) interface always lands on the Arm side.
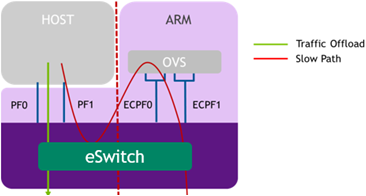
When the server and DPU are initiated, the networking to the host is blocked until the virtual switch on the DPU is loaded. Once it is loaded, traffic to the host is allowed by default.
There are two ways to pass traffic to the host interface: Either using representors to forward traffic to the host (every packet to/from the host would be handled also by the network interface on the embedded Arm side), or push rules to the embedded switch which allows and offloads this traffic.
Configuring ECPF Mode from Separated Host Mode
To enable this mode:
Start MST driver set service:
$ mst start
Identify the MST device:
$ mst status -v
Output example:
... DEVICE_TYPE MST PCI RDMA NET NUMA BlueField(rev:0) /dev/mst/<device>.1 37:00.1 mlx5_1 net-ens1f1 0 BlueField(rev:0) /dev/mst/<device> 37:00.0 mlx5_0 net-ens1f0 0
Run the following commands on the Arm:
$ mlxconfig -d /dev/mst/<device> s INTERNAL_CPU_MODEL=1
Power cycle the server.
WarningIf OVS bridges ovsbr1 and ovsbr2 are not created (you may verify that using command ovs-vsctl show), make sure field CREATE_OVS_BRIDGES is set to "yes" in /etc/mellanox/mlnx-ovs.conf.
Restricted mode is a specialization of Embedded mode and implements an additional layer of security where the host system administrator is prevented from accessing the DPU from the host. Once Restricted mode is enabled, the data center administrator should control the DPU entirely though the Arm cores and/or BMC connection instead of through the host.
For security and isolation purposes, it is possible to restrict the host from performing operations that can compromise the DPU. The following operations can be restricted individually when changing the DPU host to Restricted mode:
Port ownership – the host cannot assign itself as port owner
Hardware counters – t he host does not have access to hardware counters
Tracer functionality is blocked
RShim interface is blocked
FW flash is restricted
Enabling Host Restriction
Start the MST service.
Set restricted mode. From the Arm side, run:
$ mlxprivhost -d /dev/mst/<device> r --disable_rshim --disable_tracer --disable_counter_rd --disable_port_owner
WarningIf RShim is disabled, power cycle is required.
Disabling Host Restriction
To disable host restriction, set the mode to privileged. Run:
$ mlxprivhost -d /dev/mst/<device> p
The configuration takes effect immediately.
If reverting from "rshim-disabled" mode, system power cycle is required.
Hiding Network Ports from Host
Make sure the DPU is operating in embedded mode. Run:
# mlxconfig -d /dev/mst/<device> q | grep -i cpu INTERNAL_CPU_MODEL EMBEDDED_CPU(1)
If the output is INTERNAL_CPU_MODEL SEPERATED_HOST(0), then it means your device is operating in separated mode. See section Configuring ECPF Mode from Separated Host Mode to change this configuration.
To hide network ports from host, run:
mlxconfig -d /dev/mst/<device> s NUM_OF_PF=0
WarningPower cycle is required for this configuration to take effect.
To re-expose network ports to host, run:
mlxconfig -d /dev/mst/<device> s NUM_OF_PF=2
WarningPower cycle is required for this configuration to take effect.
In Separated mode, a network function is assigned to both the Arm cores and the x86 host cores. The ports/functions are symmetric in the sense that traffic is sent to both physical functions simultaneously. Each one of those functions has its own MAC address, which allows one to communicate with the other, and can send and receive Ethernet and RDMA over Converged Ethernet (RoCE) traffic. There is an equal bandwidth share between the two functions.
There is no dependency between the two functions. They can operate simultaneously or separately. The host can communicate with the embedded function as two separate hosts, each with its own MAC and IP addresses (configured as a standard interface).
In Separated mode, the host administrator is a trusted actor who can perform all configuration and management actions related to either network function.
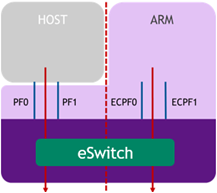
This mode enables the same operational model of a SmartNIC (that does not have a separated control plane). In this case, the Arm control plane can be used for different functions but does not have any control on the host steering functions.
The limitations of this mode are as follows:
Switchdev (virtual switch offload) mode is not supported on either of the functions
SR-IOV is only supported on the host side
Configuring Separated Host Mode from ECPF Mode
On the server host, follow these steps:
Enable separated host mode. Run:
$ mst start $ mlxconfig -d /dev/mst/<device> s INTERNAL_CPU_MODEL=0
Power cycle.
Verify configuration. Run:
$ mst start $ mlxconfig -d /dev/mst/<device> q | grep -i model
Remove OVS bridges configuration from the Arm-side. Run:
$ ovs-vsctl list-br | xargs -r -l