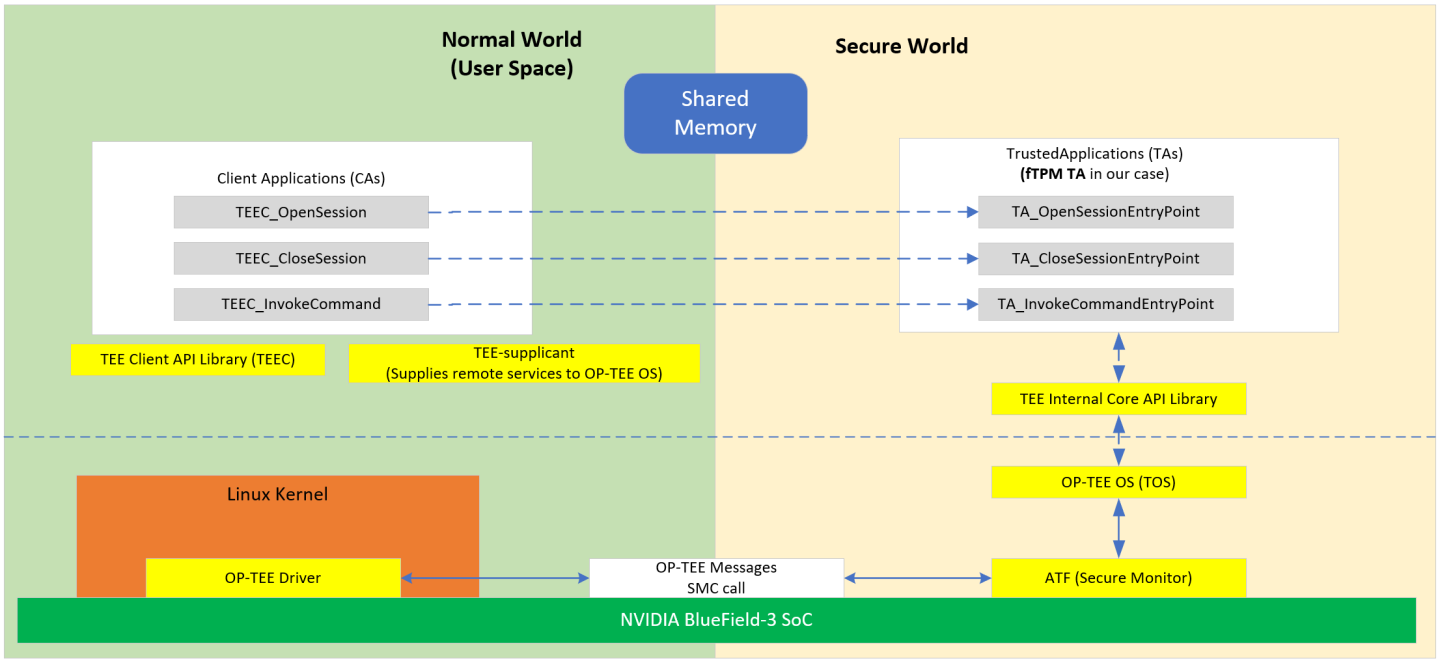
fTPM over OP-TEE
The fTPM trusted application is signed with a development key intended solely for testing purposes and is not securely signed. This feature is strictly for testing and should not be used in any operational environment.
fTMP over OP-TEE is supported on BlueField-3 only at beta level.
The Trusted Computing Group (TCG) is responsible for the specifications governing the trusted platform module (TPM). In many systems, the TPM provides integrity measurements, health checks and authentication services.
Attributes of a TPM:
- Support for bulk (symmetric) encryption in the platform
- High quality random numbers
- Cryptographic services
- Protected persistent store for small amounts of data, sticky bits, monotonic counters, and extendible registers
- Protected pseudo-persistent store for unlimited amounts of keys and data
- Extensive choice of authorization methods to access protected keys and data
- Platform identities
- Support for platform privacy
- Signing and verifying digital signatures
- Certifying the properties of keys and data
- Auditing the usage of keys and data
With TPM 2.0., the TCG creates a library specification describing all the commands or features that could be implemented and may be necessary in servers, laptops, or embedded systems. Each platform can select the features needed and the level of security or assurance required. This flexibility allows the newest TPMs to be applied to many embedded applications.
Firmware TPM (fTPM) is implemented in protected software. The code runs on the main CPU so that a separate chip is not required. While running like any other program, the code is in a protected execution environment called a trusted execution environment (TEE) which is separate from the rest of the programs running on the CPU. By doing this, secrets (e.g., private keys perhaps needed by the TPM but should not be accessed by others) can be kept in the TEE creating a more secure environment.
fTPM provides similar functionality to a chip-based TPM, but does not require extra hardware. It complies with the official TCG reference implementation of the TPM 2.0 specification . The source code of this implementation is located here.
fTPM f ully supports TPM2 Tools and the TCG TPM2 Software Stack (TSS).
Characteristics of an fTPM:
- Emulated TPM using an isolated hardware environment
- Executes in an open-source trusted execution environment (OP-TEE)
fTPM trusted application (TA) is part of the OP-TEE binary. This allows early access on bootup, runs only in secure DRAM.
NoteCurrently, the only TA supported is fTPM.
- fTPM is not a task waiting to be woken up. It only executes when TPM primitives are forwarded to it from the user space. It is guaranteed shielded execution via the TEE OS and, when invoked via the TEE Dispatcher, runs to completion.
The fTPM TA is the only TA NVIDIA® BlueField®-3 currently supports. Any TA loaded by OP-TEE must be signed (signing done externally) and then authenticated by OP-TEE before being allowed to load and execute.
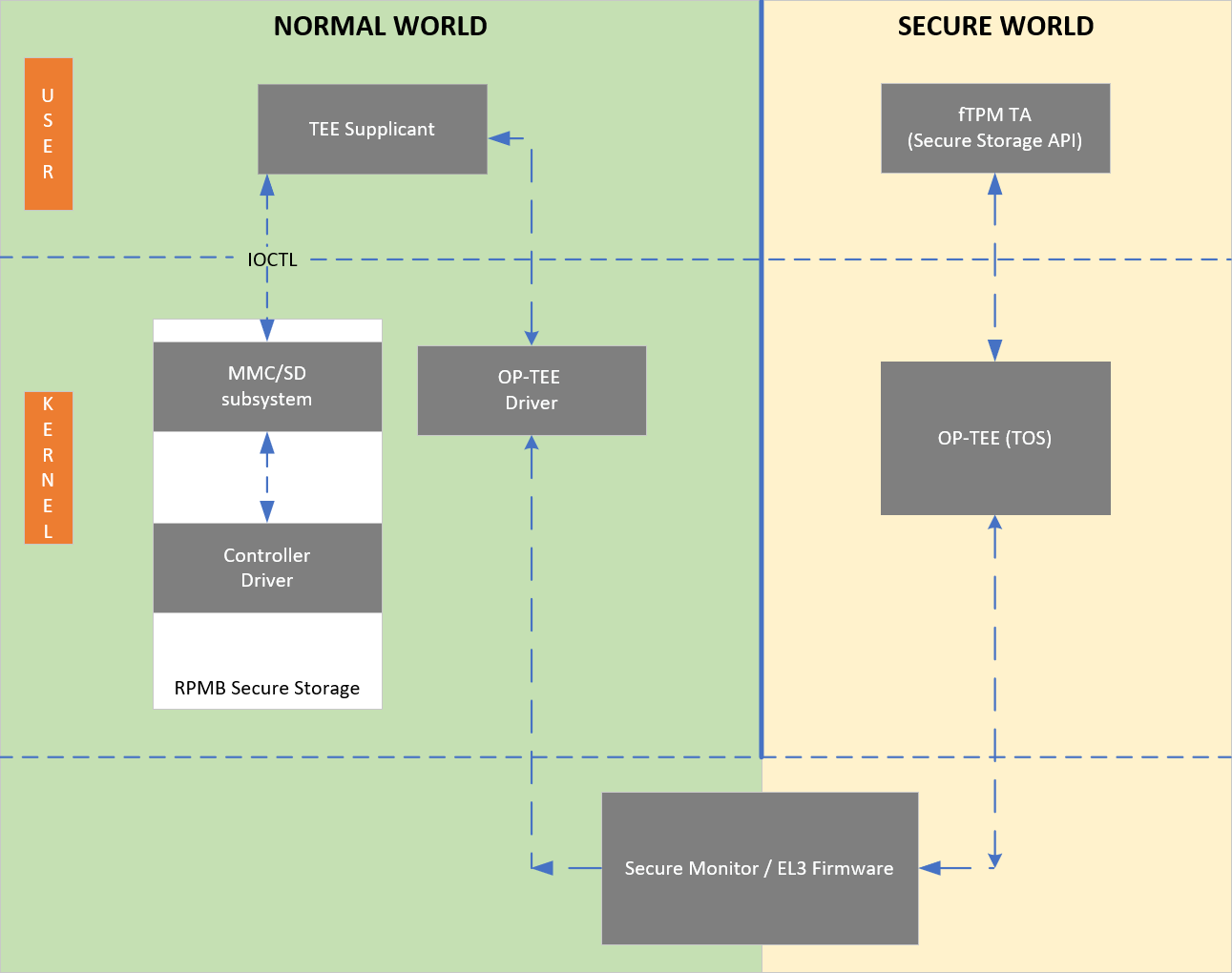
A replay-protected memory block (RPMB) is provided as a means for a system to store data to the specific memory area in an authenticated and replay-protected manner, making it readable and writable only after a successful authentication read/write accesses. The RPMB is a dedicated partition available on the eMMC, which makes it possible to store and retrieve data with integrity and authenticity support. A signed access to an RPMB is supported by first programming authentication key information to the eMMC memory (shared secret). The RPMB authentication key is programmed into the DPU at manufacturing time.
RPMB features a 4MB partition secure storage for BlueField-3.
There is no eMMC controller driver in OP-TEE. All device operations have to go through the normal world via the TEE-supplicant daemon, which relies on the Linux kernel's ioctl interface to access the device. All writes to the RPMB are atomic, authenticated, and encrypted. The RPMB partition stores data in an authenticated, replay-protected manner, making it a perfect complement to fTPM for storing and protecting data.
Enable OP-TEE in the UEFI menu:
ESC into the UEFI on DPU boot.
Navigate to Device Manager > System Configuration.
Check "Enable OP-TEE".
Save the change and reset/reboot.
Upon reboot OP-TEE is enabled.
OP-TEE is essentially dormant (does not have an OS scheduler) and reacts to external inputs.
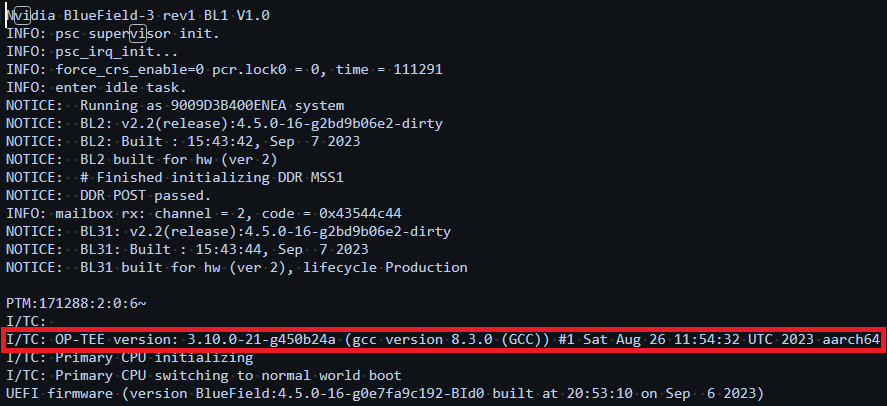
Users can see the OP-TEE version during BlueField-3 DPU boot:
The following indicators should all be present if fTPM over OP-TEE is enabled:
Check "dmesg" for the OP-TEE driver initializing
root@localhost ~]
# dmesg | grep tee[ 5.646578] optee: probingforconduit method. [ 5.653282] optee: revision 3.10 (450b24ac) [ 5.653991] optee: initialized driverVerify that the following kernel modules are loaded (running):
[root@localhost ~]
# lsmod | grep teetpm_ftpm_tee 16384 0 optee 49152 1tee49152 3 optee,tpm_ftpm_teeVerify that the proper devices are created/available (4 in total):
[root@localhost ~]
# ls -l /dev/tee*crw------- 1 root root 234, 0 Sep 8 18:24 /dev/tee0 crw------- 1 root root 234, 16 Sep 8 18:24 /dev/teepriv0 [root@localhost ~]# ls -l /dev/tpm*crw-rw---- 1 tss root 10, 224 Sep 8 18:24 /dev/tpm0 crw-rw---- 1 tss tss 252, 65536 Sep 8 18:24 /dev/tpmrm0Verify that the required processes are running (3 in total):
[root@localhost ~]
# ps axu | grep teeroot 707 0.0 0.0 76208 1372 ? Ssl 14:42 0:00 /usr/sbin/tee-supplicant root 715 0.0 0.0 0 0 ? I< 14:42 0:00 [optee_bus_scan] [root@localhost ~]# ps axu | grep tpmroot 124 0.0 0.0 0 0 ? I< 18:24 0:00 [tpm_dev_wq]